www.enlogic.com
24
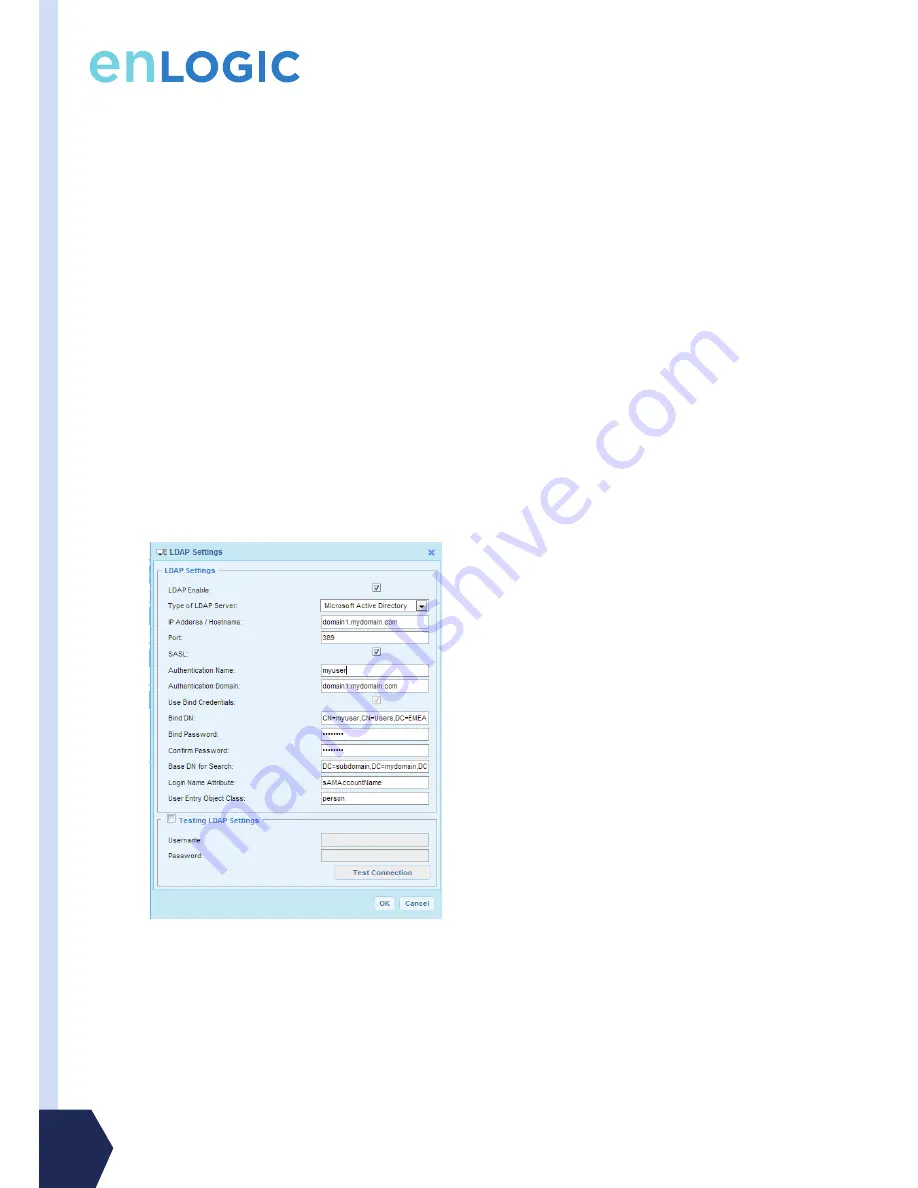
i.e.: domain1.mydomain.com
5. Enter a Port.
Note: For Microsoft, this is typically 389.
6. Select the Bind DN checkbox.
7. In the Bind DN field, enter in the account to be used to access AD.
i.e. CN=myuser,CN=Users,DC=EMEA,DC=mydomain,DC=com
8. Enter the password in the Bind Password and Confirm Password fields.
9. In the Base DN for Search field, i.e. DC=subdomain,DC=mydomain,DC=com
10. In the Login Name Attribute field, enter sAMAccountName (typically)
11. In the User Entry Object Class field, enter person.
With these LDAP settings configured, the Bind is complete.
Securing LDAP Settings (SASL)
However, with the above settings, passwords are sent in plain text. To enhance security, select the SASL option
in the LDAP Settings dialog box. This means that the PDU starts the bind process: the server replys with a key,
the PDU encrypts the password with this key and sends the encrypted text to server. Once this is done, the
server decrypts the password to perform authentication. To set SASL:
1. Make sure the Authentication Name field is the same as user name of the authenticated user.
Typically, the user name is the same as the Bind DN name, i.e., myuser.
2. In the Authentication Domain field, enter the Full Qualified Domain Name (FQDN) of the AD server.
i.e. domain1.mydomain.com
Refer to the following example for a correctly configured LDAP Settings dialog box:






























