Chapter 2: Using Windows XP
6
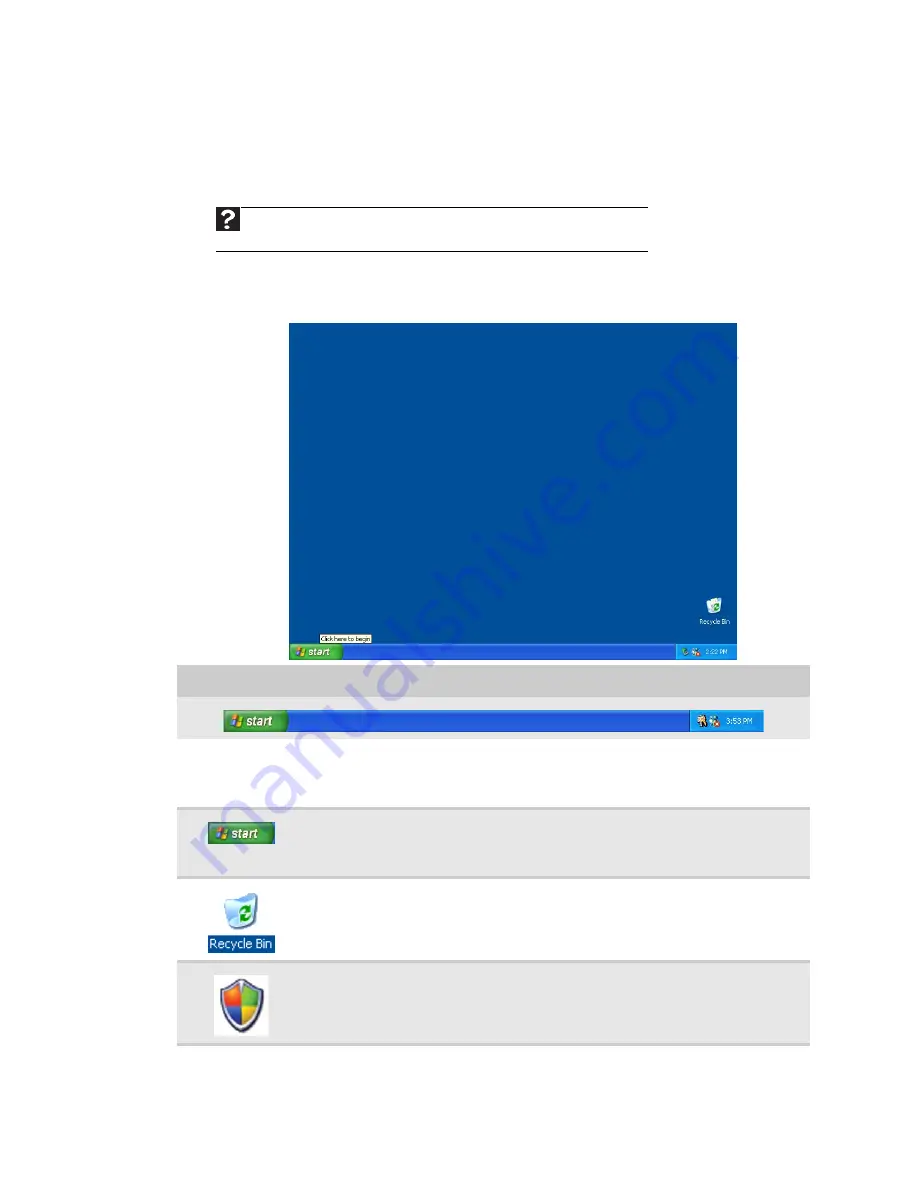
Using the Windows desktop
After your computer starts, the first screen you see is the Windows
desktop
. The
desktop is like the top of a real desk. Think of the desktop as your personalized work
space where you open programs and perform other tasks.
Your desktop may be different from this example, depending on how your computer
is set up.
The desktop contains the taskbar, the Start button, and the Recycle Bin icon.
Help
For more information about the Windows desktop
,
click Start, then click
Help and Support. Type Windows desktop in the Search box, then press E
NTER
.
Desktop elements Description
The
taskbar
is the bar at the bottom of the computer display containing the
Start button on the left and a clock on the right. Other buttons on the taskbar
represent programs that are running.
Click a program’s
button
on the taskbar to open the program’s window.
The
Start button
provides access to programs, files, help for Windows and
other programs, and computer tools and utilities.
Click the Start button, then open a file or program by clicking an item on the
menu that opens.
The
Recycle Bin
is where files, folders, and programs that you discarded are
stored. You must empty the Recycle Bin to permanently delete them from your
computer. For instructions on how to use the Recycle Bin, see
“Deleting files
and folders” on page 11
.
The Windows Security Center icon may appear on the taskbar near the clock.
The icon changes appearance to notify you when the security settings on your
computer are set below the recommended value or when updates are
available. Double-click this icon to open the Windows Security Center. For
more information, see
“Modifying security settings” on page 80
.
Summary of Contents for EL1200 Series
Page 1: ...Desktop PC User Guide...
Page 2: ......
Page 6: ...Contents iv...
Page 36: ...Chapter 3 Using the Internet and Faxing 30...
Page 50: ...Chapter 4 Playing and Creating Media Files 44...
Page 62: ...Chapter 5 Networking Your Computer 56...
Page 79: ...Chapter 7 73 Computer Hardware security Data security Security updates Protecting Your...
Page 90: ...Chapter 7 84...



























