DSA-6100 User Guide
20
y
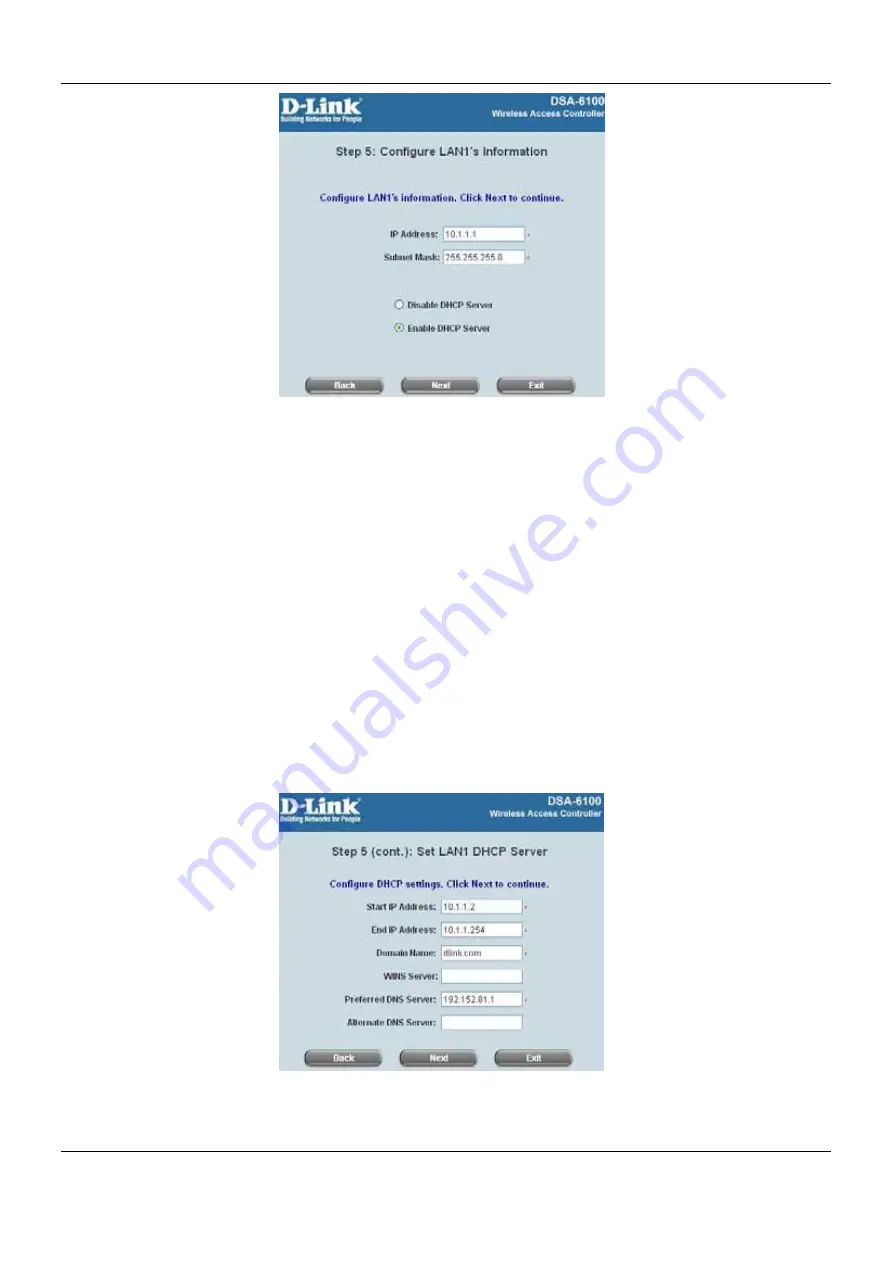
Step 5 (cont.): Set LAN1 DHCP Server
If the
Enable DHCP Server
option is selected, more information about the LAN1 DHCP server will be needed.
Fields marked with red asterisks must be filled in.
Start IP Address:
The start IP address of the DHCP scope of LAN1.
End IP Address:
The end IP address of the DHCP scope of LAN1.
These IP address will be assigned to the LAN1 clients.
(Note: Be sure that IP address assigned in this
range is NOT used in other setting of DSA-6100.)
Domain Name:
Enter a domain name provided by your ISP (e.g. dlink.com).
WINS Server:
Enter the IP address of the WINS server.(Windows Internet Naming Service Server) This field
is optional.
Preferred DNS Server:
The DNS Server settings are provided by your ISP. Only the Preferred DNS Server
field is mandatory. Contact your ISP if you are unsure of the DNS Server settings.
Alternate DNS Server:
The DNS Server settings are provided by your ISP. The field is optional. Click
Next
to
continue.






























