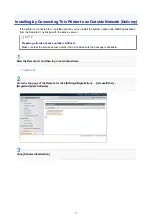
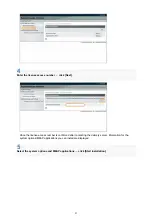
- 54 -
straightforwardly into another language. (Hereinafter, translation is included without limitation in the term
"modification".)
"Source code" for a work means the preferred form of the work for making modifications to it. For a library,
complete source code means all the source code for all modules it contains, plus any associated interface
definition files, plus the scripts used to control compilation and installation of the library.
Activities other than copying, distribution and modification are not covered by this License; they are outside its
scope. The act of running a program using the Library is not restricted, and output from such a program is
covered only if its contents constitute a work based on the Library (independent of the use of the Library in a
tool for writing it). Whether that is true depends on what the Library does and what the program that uses the
Library does.
1. You may copy and distribute verbatim copies of the Library's complete source code as you receive it, in any
medium, provided that you conspicuously and appropriately publish on each copy an appropriate copyright
notice and disclaimer of warranty; keep intact all the notices that refer to this License and to the absence of any
warranty; and distribute a copy of this License along with the Library.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer warranty
protection in exchange for a fee.
2. You may modify your copy or copies of the Library or any portion of it, thus forming a work based on the
Library, and copy and distribute such modifications or work under the terms of Section 1 above, provided that
you also meet all of these conditions:
•
a) The modified work must itself be a software library.
•
b) You must cause the files modified to carry prominent notices stating that you changed the files and
the date of any change.
•
c) You must cause the whole of the work to be licensed at no charge to all third parties under the terms
of this License.
•
d) If a facility in the modified Library refers to a function or a table of data to be supplied by an
application program that uses the facility, other than as an argument passed when the facility is
invoked, then you must make a good faith effort to ensure that, in the event an application does not
supply such function or table, the facility still operates, and performs whatever part of its purpose
remains meaningful.
(For example, a function in a library to compute square roots has a purpose that is entirely well-defined
independent of the application. Therefore, Subsection 2d requires that any application-supplied
function or table used by this function must be optional: if the application does not supply it, the square
root function must still compute square roots.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are not derived
from the Library, and can be reasonably considered independent and separate works in themselves, then this
License, and its terms, do not apply to those sections when you distribute them as separate works. But when
Summary of Contents for LBP710Cx
Page 1: ...LBP712Cx LBP710Cx User s Guide USRMA 0722 00 2016 04 en Copyright CANON INC 2016 ...
Page 51: ...Paper P 620 Basic Operations 45 ...
Page 58: ...4 on 1 Postcard Insert the postcard with the upper end toward the machine Basic Operations 52 ...
Page 78: ...Printing a Document 72 ...
Page 93: ...LINKS Basic Printing Operations P 73 Printing a Document 87 ...
Page 97: ...LINKS Basic Printing Operations P 73 Enlarging or Reducing P 82 Printing a Document 91 ...
Page 108: ...LINKS Basic Printing Operations P 73 Printing a Document 102 ...
Page 140: ...LINKS Using the Encrypted Print P 135 Installing an SD Card P 633 Printing a Document 134 ...
Page 195: ...LINKS Connecting to a Network P 186 Network 189 ...
Page 250: ...LINKS Entering Sleep Mode P 63 Network 244 ...
Page 290: ...Printing a Document Stored in the Machine Stored Job Print P 136 Security 284 ...
Page 296: ... Functions of the Keys Operation Panel P 24 Security 290 ...
Page 334: ...Using TLS for Encrypted Communications P 297 Configuring IPSec Settings P 301 Security 328 ...
Page 344: ...Using Remote UI 338 ...
Page 359: ...LINKS Remote UI Screens P 339 Using Remote UI 353 ...
Page 383: ...Paper Source 0YSF 05E See Select Feeder Menu P 500 Setting Menu List 377 ...
Page 516: ...Troubleshooting 510 ...
Page 600: ...LINKS Utility Menu P 491 Job Menu P 496 Maintenance 594 ...
Page 611: ...Third Party Software 0YSF 090 Appendix 605 ...
Page 630: ...Appendix 624 ...
Page 651: ...Manual Display Settings 0YSF 091 Appendix 645 ...
Page 675: ...Scalable Fonts PCL Appendix 669 ...
Page 676: ...Appendix 670 ...
Page 677: ...Appendix 671 ...
Page 678: ...OCR Code Scalable Fonts PCL Bitmapped Fonts PCL Appendix 672 ...
Page 701: ... 16 MD4 RSA Data Security Inc MD4 Message Digest Algorithm ...
Page 712: ... 27 including the GNU Public Licence ...
Page 736: ... 51 SOFTWARE ...
Page 749: ...Search Enter keyword s here 1 ...
Page 752: ...2 ...
Page 762: ...12 ...
Page 768: ...3 Click Delivered Update 4 Click Apply Firmware 5 Confirm the firmware to apply click Yes 5 ...
Page 770: ...3 Click Delivered Update 4 Click Delete Firmware 7 ...
Page 789: ...Search Enter keyword s here 1 ...
Page 810: ...Starting MEAP Applications Stopping MEAP Applications Starting Stopping MEAP Applications 10 ...
Page 818: ...4 Click License Management 5 18 ...
Page 821: ...4 Click License Management 5 21 ...
Page 822: ...Click Disable 6 Click Yes The license file is disabled 22 ...
Page 824: ...4 Click License Management 5 24 ...
Page 827: ...4 Click License Management 5 27 ...
Page 828: ...Click Delete 6 Click Yes The license file is deleted 28 ...
Page 830: ...4 Click Authentication Information Settings 5 30 ...
Page 832: ...When cancelling authentication information Click Delete 32 ...
Page 837: ...5 ...
Page 846: ...14 ...
Page 849: ...17 ...
Page 855: ...4 Click Yes The setting information of the application is deleted 23 ...