T1 AND E1 REMOTE ACCESS CONCENTRATORS
38
4.3.3 A
UTHENTICATION
S
ETTINGS
To configure the Remote Access Concentrator’s Authentication Settings, take these steps:
1. Select Module Configuration from the Local Management utility’s Module Menu.
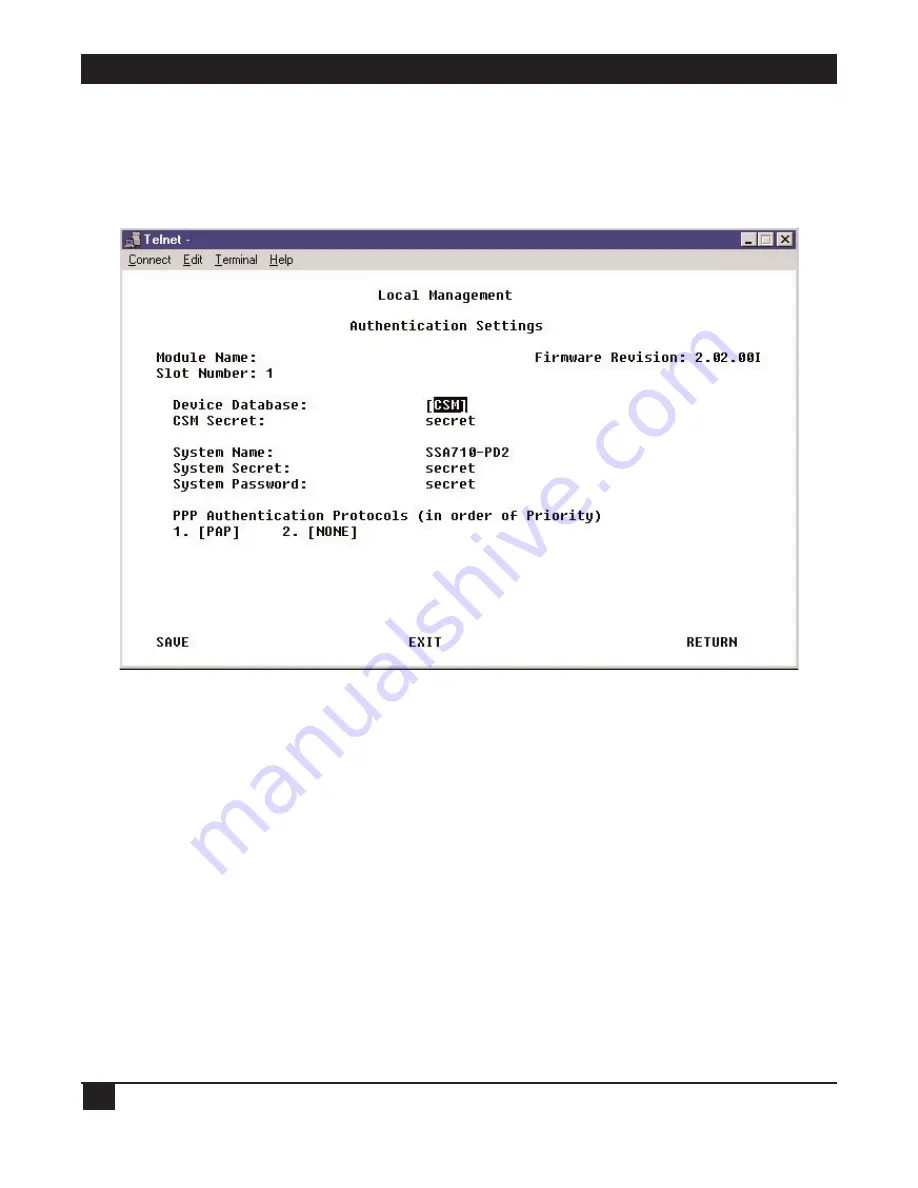
2. Select Authentication Settings from the Module Configuration menu. This screen will appear:
3. Select the type of Device Database you’ll be using. The device database stores remote-device data used
for device authentication. Use the space bar to toggle your selection between either RADIUS (if you’ll be
using an RFC-2138-compliant RADIUS server) or CSM (if you’ll be using CSM for device authentication).
Note that CSM not only performs traditional authentication tasks, it also allows for more advanced policy
management and flow accounting.
Steps 4 through 7 concern CSM and call-out functions only; if you’ve chosen RADIUS as your device database,
skip to step 8. (You’ll use the Local Management utility’s RADIUS menu to configure the authentication
information—a shared secret—required for the Concentrator to interact with RADIUS; see
Section 4.3.5
.)
NOTE
The CSM Secret, System Name, and System Secret you’ll set in steps 4 through 6 must
match those configured through CSM (under the Properties tab of CSM’s Access
Server option). Refer to CSM’s HTML documentation.
4. Enter the CSM Secret. This is the CHAP secret shared between CSM and the Concentrator and used
for authentication negotiation.
5. Enter a unique System Name for the Concentrator.






























