Using Device tabs to configure the security gateway
Issue 4 May 2005
69
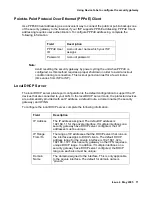
To set the amount of time delay to switch from a secondary interface to the primary interface
once the primary link has been detected, configure the Hold Down Timer. This delay provides
the necessary time for the primary interface to stabilize. The Hold Down Timer applies to
failover conditions occurring due to a link-level failure on the public primary interface only.
The Hold Down Time value is expressed in seconds. The value range is 0 to 3600 seconds. The
default value is 60 seconds.
Note:
Note:
There is a scenario in which the switchover from the public backup interface to
the public interface will occur before the hold down timer has expired. If the idle
timer is set to a value less than that of the hold down timer, and the public primary
interface link becomes available while at roughly the same time traffic ceases to
flow through the public backup interface, the switchover will occur when the idle
time expires rather than when the hold down timer expires.
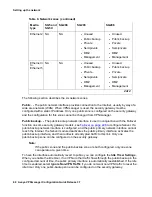
Private. - The private network interface usually provides connection to your private local area
network (LAN) or your corporate LAN. The private network interface can be configured with
Static, DHCP Server or DHCP Relay.
Semi-private. - The semi-private network interface provides connection to a network whose
equipment can be made physically secure, but whose medium is vulnerable to attack, such as a
wireless network used within a corporation’s private network infrastructure). Traffic on the
semi-private interface is usually encrypted. Only one semi-private zone can be configured on
the security gateway.
DMZ. - The demilitarized zone (DMZ) network interface is usually used to provide Internet
users with access to some corporate services without compromising the private network where
sensitive information is stored. A DMZ network contains resources such as Web servers, FTP
servers, and SMTP (e-mail) servers. Because DMZ networks are vulnerable to attack (that is
denial of service), corporations usually add additional security devices such as intrusion
detection systems, virus scanners, and so on. Only one DMZ zone can be configured on the
device.
Management. - The management interface connection can be configured to simplify network
deployments, to eliminate enterprise network dependencies on switches or routers. The
management network interface is usually used as an access point for a dedicated VPNmanager
management station or as a dedicated interface for dumping log messages to a syslog server.
Summary of Contents for 3.7
Page 1: ...VPNmanager Configuration Guide Release 3 7 670 100 600 Issue 4 May 2005...
Page 4: ......
Page 20: ...Preface 20 Avaya VPNmanager Configuration Guide Release 3 7...
Page 32: ...Overview of implementation 32 Avaya VPNmanager Configuration Guide Release 3 7...
Page 53: ...Preferences Issue 4 May 2005 53 Figure 16 Tunnel End Point Policy...
Page 54: ...Using VPNmanager 54 Avaya VPNmanager Configuration Guide Release 3 7...
Page 244: ...Using advanced features 244 Avaya VPNmanager Configuration Guide Release 3 7...
Page 292: ...Upgrading firmware and licenses 292 Avaya VPNmanager Configuration Guide Release 3 7...