Отзывы:
Нет отзывов
Похожие инструкции для HiPath C10

M180
Бренд: Haier Страницы: 24

X400
Бренд: Panasonic Страницы: 48

SCH-R970C
Бренд: Samsung Страницы: 251

G99
Бренд: chinavasion Страницы: 44

P1010
Бренд: Pantech Страницы: 51

H1915
Бренд: HTC Страницы: 36
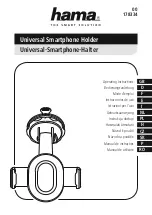
178334
Бренд: Hama Страницы: 27

5380ip
Бренд: Aastra Страницы: 24

Idol4 S VF
Бренд: TCL Страницы: 74

BluPTT-Mini
Бренд: Klein Electronics Страницы: 2

G2x
Бренд: T-Mobile Страницы: 25

P5 Pro
Бренд: Allview Страницы: 7

VPS-804P
Бренд: Slican Страницы: 50

ADR910L
Бренд: Pantech Страницы: 213

Soundpoint 335
Бренд: Polycom Страницы: 9

5215
Бренд: Mitel Страницы: 42

F24
Бренд: Hisense Страницы: 27

CONFERENCE MAX NDA-31109
Бренд: NEC Страницы: 5

















