Chapter 14 Certificates
293
Nortel Business Secure Router 252 Configuration — Basics
Valid To
This field displays the date that the certificate expires. The text
displays in red and includes an Expiring! or Expired! message if the
certificate is about to expire or has already expired.
Key Algorithm
This field displays the type of algorithm that was used to generate
the certificate key pair (the Business Secure Router uses RSA
encryption) and the length of the key set in bits (1 024-bits, for
example).
Subject Alternative
Name
This (optional) field displays the certificate owner‘s IP address (IP),
domain name (DNS), or e-mail address (EMAIL).
Key Usage
This field displays for what functions the certificate key can be used.
For example, DigitalSignature means that the key can be used to
sign certificates and KeyEncipherment means that the key can be
used to encrypt text.
Basic Constraint
This field displays general information about the certificate. For
example, Subject Type=CA means that this is a certification authority
certificate and Path Length Constraint=1 means that there can only
be one certification authority in the certification path of the certificate.
MD5 Fingerprint
This is the message digest of the certificate that the Business Secure
Router calculated using the MD5 algorithm. You cannot use this
value to verify that this is the remote host’s actual certificate because
the Business Secure Router has signed the certificate; thus causing
this value to be different from that of the remote host’s actual
certificate. See
“Verifying a certificate of a trusted remote host” on
for how to verify a remote host’s certificate.
SHA1 Fingerprint
This is the message digest of the certificate that the Business Secure
Router calculated using the SHA1 algorithm. You cannot use this
value to verify that this is the remote host’s actual certificate because
the Business Secure Router has signed the certificate; thus causing
this value to be different from that of the remote host’s actual
certificate. See
“Verifying a certificate of a trusted remote host” on
for how to verify a remote host’s certificate.
Certificate in PEM
(Base-64)
Encoded Format
This read-only text box displays the certificate or certification request
in Privacy Enhanced Mail (PEM) format. PEM uses 64 ASCII
characters to convert the binary certificate into a printable form.
You can copy and paste the certificate into an e-mail to send to
friends or colleagues or you can copy and paste the certificate into a
text editor and save the file on a management computer for later
distribution (through floppy disk for example).
Export
Click this button and then
Save
in the
File Download
screen. The
Save As
screen displays. Browse to the location that you want to
use and click
Save
.
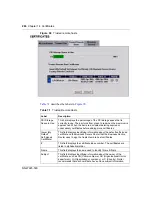
Table 73
Trusted remote host details
Label
Description
Содержание BSR252
Страница 28: ...28 Tables NN47923 500 ...
Страница 44: ...44 Chapter 1 Getting to know your Business Secure Router NN47923 500 ...
Страница 52: ...52 Chapter 2 Introducing the WebGUI NN47923 500 ...
Страница 70: ...70 Chapter 3 Wizard setup NN47923 500 ...
Страница 91: ...Chapter 5 System screens 91 Nortel Business Secure Router 252 Configuration Basics Figure 20 Time and Date ...
Страница 96: ...96 Chapter 5 System screens NN47923 500 ...
Страница 100: ...100 Chapter 6 LAN screens NN47923 500 Configuring IP Click LAN to open the IP screen Figure 22 LAN IP ...
Страница 111: ...Chapter 7 WAN screens 111 Nortel Business Secure Router 252 Configuration Basics Figure 26 WAN WAN ISP ...
Страница 114: ...114 Chapter 7 WAN screens NN47923 500 Figure 27 WAN IP ...
Страница 120: ...120 Chapter 7 WAN screens NN47923 500 Figure 31 Dial Backup Setup ...
Страница 128: ...128 Chapter 7 WAN screens NN47923 500 ...
Страница 152: ...152 Chapter 9 Static Route screens NN47923 500 ...
Страница 194: ...194 Chapter 11 Firewall screens NN47923 500 ...
Страница 210: ...210 Chapter 13 VPN NN47923 500 Figure 67 Summary IP Policies ...
Страница 222: ...222 Chapter 13 VPN NN47923 500 Figure 71 VPN Branch Office rule setup ...
Страница 231: ...Chapter 13 VPN 231 Nortel Business Secure Router 252 Configuration Basics Figure 72 VPN Branch Office IP Policy ...
Страница 249: ...Chapter 13 VPN 249 Nortel Business Secure Router 252 Configuration Basics Figure 78 VPN Client Termination ...
Страница 256: ...256 Chapter 13 VPN NN47923 500 Figure 81 VPN Client Termination advanced ...
Страница 260: ...260 Chapter 13 VPN NN47923 500 ...
Страница 264: ...264 Chapter 14 Certificates NN47923 500 Figure 83 My Certificates ...
Страница 270: ...270 Chapter 14 Certificates NN47923 500 Figure 85 My Certificate create ...
Страница 274: ...274 Chapter 14 Certificates NN47923 500 Figure 86 My Certificate details ...
Страница 282: ...282 Chapter 14 Certificates NN47923 500 Figure 89 Trusted CA details ...
Страница 298: ...298 Chapter 14 Certificates NN47923 500 ...
Страница 316: ...316 Chapter 16 IEEE 802 1x NN47923 500 ...
Страница 320: ...320 Chapter 17 Authentication server NN47923 500 Figure 106 Local User database edit ...
Страница 328: ...328 Chapter 17 Authentication server NN47923 500 ...
Страница 376: ...376 Chapter 20 Logs Screens NN47923 500 Figure 150 Log settings ...
Страница 386: ...386 Chapter 20 Logs Screens NN47923 500 ...
Страница 392: ...392 Chapter 21 Call scheduling screens NN47923 500 Figure 157 Applying Schedule Sets to a remote node ...
Страница 393: ...Chapter 21 Call scheduling screens 393 Nortel Business Secure Router 252 Configuration Basics ...
Страница 394: ...394 Chapter 21 Call scheduling screens NN47923 500 ...
Страница 409: ...Chapter 22 Maintenance 409 Nortel Business Secure Router 252 Configuration Basics Figure 170 Restart screen ...
Страница 410: ...410 Chapter 22 Maintenance NN47923 500 ...
Страница 430: ...430 Appendix A Troubleshooting NN47923 500 ...