244
Chapter 13 VPN
NN47923-500
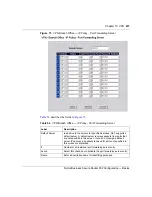
Multiple Proposal Select this check box to allow the Business Secure Router to use any
of its phase 2 encryption and authentication algorithms when
negotiating an IPSec SA.
Clear this check box to have the Business Secure Router use only the
phase 2 encryption and authentication algorithms when negotiating an
IPSec SA.
Active Protocol
Select
ESP
or
AH
from the drop-down list. The Business Secure
Router's IPSec Protocol must be identical to the remote IPSec router.
The ESP (Encapsulation Security Payload) protocol (RFC 2406)
provides encryption as well as the authentication offered by AH. If you
select
ESP
here, you must select options from the Encryption
Algorithm and Authentication Algorithm fields. The AH protocol
(Authentication Header Protocol) (RFC 2402) was designed for
integrity, authentication, sequence integrity (replay resistance), and
nonrepudiation, but not for confidentiality, for which the ESP was
designed. If you select
AH
here, you must select options from the
Authentication Algorithm
field.
Encryption
Algorithm
Select
DES
,
3DES
,
AES
or
NULL
from the drop-down list.
When you use one of these encryption algorithms for data
communications, both the sending device and the receiving device
must use the same secret key, which can be used to encrypt and
decrypt the message or to generate and verify a message
authentication code. The DES encryption algorithm uses a 56-bit key.
Triple DES (
3DES
) is a variation on DES that uses a 168-bit key. As a
result,
3DES
is more secure than
DES
. It also requires more
processing power, resulting in increased latency and decreased
throughput. You can select a 128-bit, 192-bit, or 256-bit key with this
implementation of
AES
.
AES
is faster than
3DES
.
Select
NULL
to set up a tunnel without encryption. When you select
NULL
, you do not enter an encryption key.
Authentication
Algorithm
Select
SHA1
or
MD5
from the drop-down list. MD5 (Message Digest
5) and SHA1 (Secure Hash Algorithm) are hash algorithms used to
authenticate packet data. The SHA1 algorithm is generally considered
stronger than MD5, but is slower. Select MD5 for minimal security and
SHA-1 for maximum security.
SA Life Time
Define the length of time before an IKE SA automatically renegotiates
in this field. It can range from 60 to 3 000 000 seconds (almost 35
days). A short SA life time increases security by forcing the two IPSec
routers to update the encryption and authentication keys. However,
every time the VPN tunnel renegotiates, all users accessing remote
resources are temporarily disconnected.
Encapsulation
Select
Tunnel
mode or
Transport
mode from the drop-down list. The
Business Secure Router's encapsulation mode must be identical to
the remote IPSec router.
Tunnel
is compatible with NAT,
Transport
is
not.
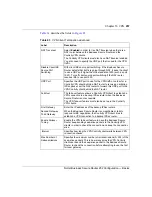
Table 57
VPN Branch Office Advanced Rule Setup
Label
Description
Содержание BSR252
Страница 28: ...28 Tables NN47923 500 ...
Страница 44: ...44 Chapter 1 Getting to know your Business Secure Router NN47923 500 ...
Страница 52: ...52 Chapter 2 Introducing the WebGUI NN47923 500 ...
Страница 70: ...70 Chapter 3 Wizard setup NN47923 500 ...
Страница 91: ...Chapter 5 System screens 91 Nortel Business Secure Router 252 Configuration Basics Figure 20 Time and Date ...
Страница 96: ...96 Chapter 5 System screens NN47923 500 ...
Страница 100: ...100 Chapter 6 LAN screens NN47923 500 Configuring IP Click LAN to open the IP screen Figure 22 LAN IP ...
Страница 111: ...Chapter 7 WAN screens 111 Nortel Business Secure Router 252 Configuration Basics Figure 26 WAN WAN ISP ...
Страница 114: ...114 Chapter 7 WAN screens NN47923 500 Figure 27 WAN IP ...
Страница 120: ...120 Chapter 7 WAN screens NN47923 500 Figure 31 Dial Backup Setup ...
Страница 128: ...128 Chapter 7 WAN screens NN47923 500 ...
Страница 152: ...152 Chapter 9 Static Route screens NN47923 500 ...
Страница 194: ...194 Chapter 11 Firewall screens NN47923 500 ...
Страница 210: ...210 Chapter 13 VPN NN47923 500 Figure 67 Summary IP Policies ...
Страница 222: ...222 Chapter 13 VPN NN47923 500 Figure 71 VPN Branch Office rule setup ...
Страница 231: ...Chapter 13 VPN 231 Nortel Business Secure Router 252 Configuration Basics Figure 72 VPN Branch Office IP Policy ...
Страница 249: ...Chapter 13 VPN 249 Nortel Business Secure Router 252 Configuration Basics Figure 78 VPN Client Termination ...
Страница 256: ...256 Chapter 13 VPN NN47923 500 Figure 81 VPN Client Termination advanced ...
Страница 260: ...260 Chapter 13 VPN NN47923 500 ...
Страница 264: ...264 Chapter 14 Certificates NN47923 500 Figure 83 My Certificates ...
Страница 270: ...270 Chapter 14 Certificates NN47923 500 Figure 85 My Certificate create ...
Страница 274: ...274 Chapter 14 Certificates NN47923 500 Figure 86 My Certificate details ...
Страница 282: ...282 Chapter 14 Certificates NN47923 500 Figure 89 Trusted CA details ...
Страница 298: ...298 Chapter 14 Certificates NN47923 500 ...
Страница 316: ...316 Chapter 16 IEEE 802 1x NN47923 500 ...
Страница 320: ...320 Chapter 17 Authentication server NN47923 500 Figure 106 Local User database edit ...
Страница 328: ...328 Chapter 17 Authentication server NN47923 500 ...
Страница 376: ...376 Chapter 20 Logs Screens NN47923 500 Figure 150 Log settings ...
Страница 386: ...386 Chapter 20 Logs Screens NN47923 500 ...
Страница 392: ...392 Chapter 21 Call scheduling screens NN47923 500 Figure 157 Applying Schedule Sets to a remote node ...
Страница 393: ...Chapter 21 Call scheduling screens 393 Nortel Business Secure Router 252 Configuration Basics ...
Страница 394: ...394 Chapter 21 Call scheduling screens NN47923 500 ...
Страница 409: ...Chapter 22 Maintenance 409 Nortel Business Secure Router 252 Configuration Basics Figure 170 Restart screen ...
Страница 410: ...410 Chapter 22 Maintenance NN47923 500 ...
Страница 430: ...430 Appendix A Troubleshooting NN47923 500 ...