44
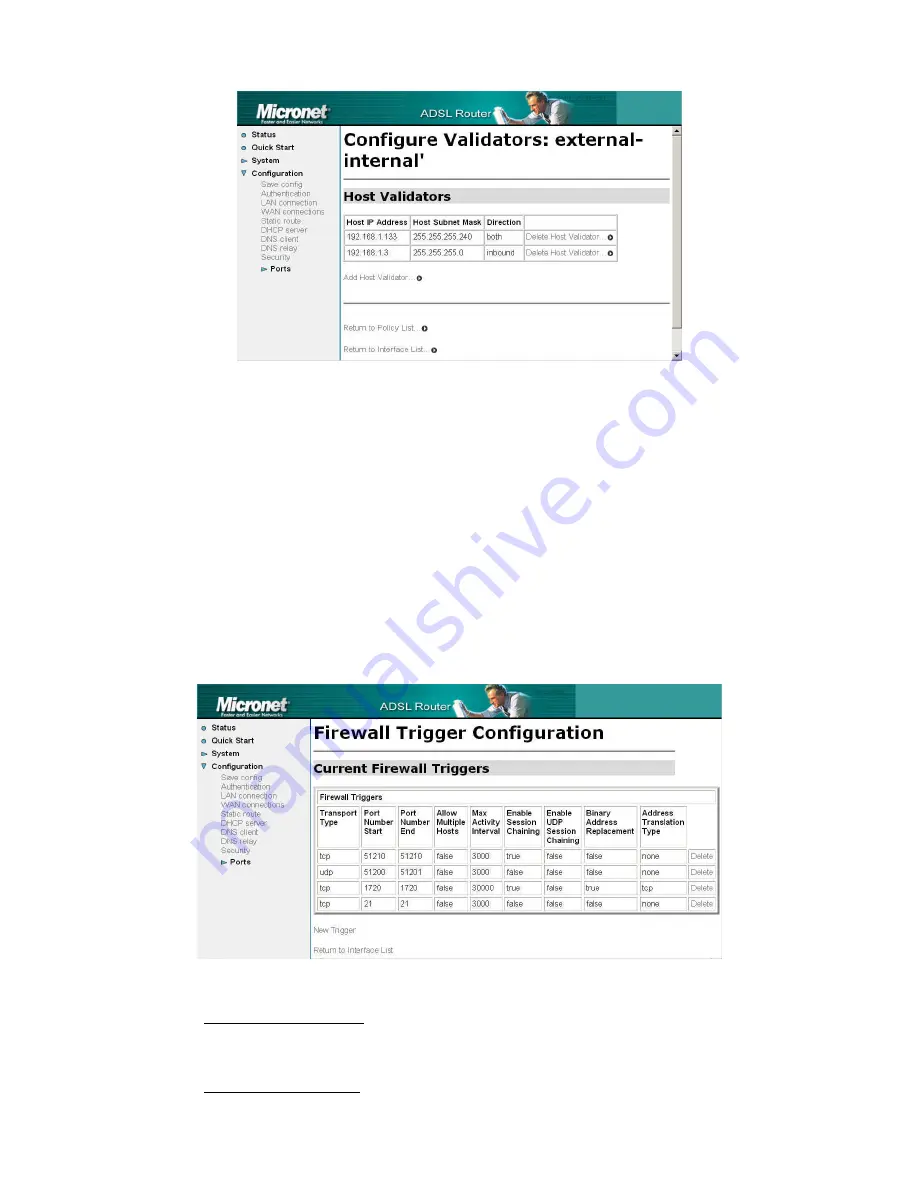
6.5.Firewall Trigger Configuration:
Security triggers are used to deal with application protocols that create
separate sessions. Some application protocols open secondary
connections during normal operations. The most common example of this
is FTP. Rather than allowing a range or port numbers, triggers handle the
situation dynamically, allowing the secondary sessions on when
appropriate. After selecting a security level, the preset Firewall Triggers
are implemented.
Allow Multiple Hosts
Allows multiple hosts to use the same port or not.
Max Activity Interval
















































