Chapter 23
Kerio VPN
292
Name of the tunnel
Each VPN tunnel must have a unique name. This name will be used in the table of inter-
faces, in traffic rules (see chapter
) and interface statistics (details in chapter
).
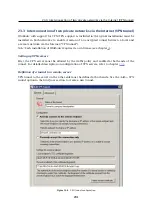
Configuration
Selection of a mode for the local end of the tunnel:
•
Active
— this side of the tunnel will automatically attempt to establish and main-
tain a connection to the remote VPN server.
The remote VPN server specification is required through the
Remote hostname
or IP address
entry.
If the remote VPN server does not use the port
4090
,
a corresponding port number separated by a colon must be specified (e.g.
server.company.com:4100
or
10.10.100.20:9000
).
This mode is available if the IP address or DNS name of the other side of the
tunnel is known and the remote endpoint is allowed to accept incoming connec-
tions (i.e. the communication is not blocked by a firewall at the remote end of the
tunnel).
•
Passive
— this end of the tunnel will only listen for an incoming connection from
the remote (active) side.
The passive mode is only useful when the local end of the tunnel has a fixed IP
address and when it is allowed to accept incoming connections.
At least one end of each VPN tunnel must be switched to the active mode (passive servers
cannot initialize connection).
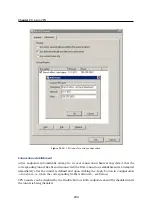
Configuration of a remote end of the tunnel
When a VPN tunnel is being created, identity of the remote endpoint is authenticated
through the fingerprint of its SSL certificate. If the fingerprint does not match with the
fingerprint specified in the configuration of the tunnel, the connection will be rejected.
The fingerprint of the local certificate and the entry for specification of the remote fin-
gerprint are provided in the
Settings for remote endpoint
section. Specify the fingerprint
for the remote VPN server certificate and vice versa — specify the fingerprint of the local
server in the configuration at the remote server.
If the local endpoint is set to the active mode, the certificate of the remote endpoint and
its fingerprint can be downloaded by clicking
Detect remote certificate
. Passive endpoint
cannot detect remote certificate.
However, this method of fingerprint setting is quite insecure —a counterfeit certificate
might be used. If a fingerprint of a false certificate is used for the configuration of
the VPN tunnel, it is possible to create a tunnel for the false endpoint (for the attacker).
Moreover, a valid certificate would not be accepted from the other side. Therefore, for
security reasons, it is recommended to set fingerprints manually.
Содержание KERIO WINROUTE FIREWALL 6
Страница 1: ...Kerio WinRoute Firewall 6 Administrator s Guide Kerio Technologies s r o...
Страница 157: ...12 3 Content Rating System Kerio Web Filter 157 Figure 12 7 Kerio Web Filter rule...
Страница 189: ...14 4 URL Groups 189 Description The item s description comments and notes for the administrator...
Страница 247: ...19 4 Alerts 247 Figure 19 14 Details of a selected event...
Страница 330: ...Chapter 23 Kerio VPN 330 Figure 23 55 The Paris filial office VPN server configuration...
Страница 368: ...368...