24
2.1
Installation Modes
F-Secure Anti-Virus for Microsoft Exchange can be installed either in
stand-alone or centrally administered mode. In stand-alone installation,
F-Secure Anti-Virus for Microsoft Exchange is managed with Web
Console. In centrally administered mode, it is managed centrally with
F-Secure Policy Manager components: F-Secure Policy Manager Server
and F-Secure Policy Manager Console.
To administer F-Secure Anti-Virus for Microsoft Exchange in the centrally
administered mode, you have to install the following components:
F-Secure Policy Manager Server (on a dedicated machine)
F-Secure Policy Manager Console (on the administrator's
machine)
2.2
Network Requirements
This network configuration is valid for all scenarios described in this
chapter. Make sure that the following network traffic can travel:
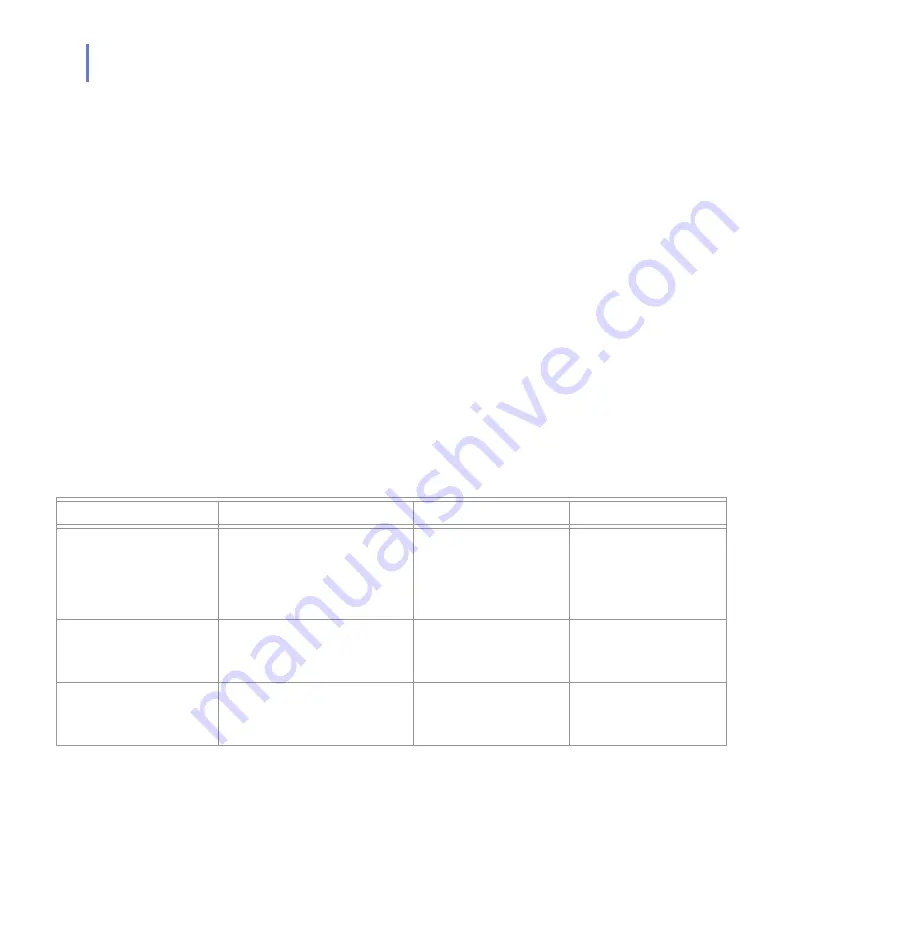
Service
Process
Inbound ports
Outbound ports
F-Secure Content Scanner
Server
%ProgramFiles%\F-Secure\
Content Scanner Server\
fsavsd.exe
18971 (TCP) +
1024-65536 (TCP), only
with F-Secure Anti-Virus
for Internet Mail on a
separate host
DNS (53, UDP/TCP),
HTTP (80) or other known
port used for HTTP proxy
F-Secure Anti-Virus for
Microsoft Exchange Web
Console
%ProgramFiles%\F-Secure\
Web User Interface\
bin\fswebuid.exe
25023
DNS (53, UDP and TCP),
1433 (TCP), only with the
dedicated SQL server
F-Secure Automatic
Update Agent
F-Secure Automatic Update.exe
371 (UDP), only if
BackWeb Polite Protocol
is used
DNS (53, UDP and TCP),
HTTP (80)
Содержание ANTI-VIRUS FOR MICROSOFT EXCHANGE 6.62 -
Страница 1: ...F Secure Anti Virus for Microsoft Exchange Administrator s Guide ...
Страница 9: ...9 ABOUT THIS GUIDE How This Guide Is Organized 10 Conventions Used in F Secure Guides 13 ...
Страница 23: ...23 2 DEPLOYMENT Installation Modes 24 Network Requirements 24 Deployment Scenarios 25 ...
Страница 41: ...CHAPTER3 41 Installation Click Next to continue Step 3 Read the licence agreement ...
Страница 44: ...44 Step 6 Choose the destination folder for the installation Click Next to continue ...
Страница 56: ...56 Step 16 The list of components that will be installed is displayed Click Start to install listed components ...
Страница 57: ...CHAPTER3 57 Installation Step 17 The installation status of the components is displayed Click Next to continue ...
Страница 134: ...134 Inbound Mail Figure 5 4 Real Time Processing Virus Scanning Inbound Mail settings ...
Страница 138: ...138 Outbound Figure 5 5 Real Time Processing Virus Scanning Outbound Mail settings ...
Страница 142: ...142 Figure 5 6 Real Time Processing Virus Scanning Public Folders settings ...
Страница 152: ...152 Figure 5 9 Real Time Processing Content Blocking Inbound Mail Content Filtering settings ...
Страница 178: ...178 5 2 5 Quarantine Figure 5 17 Quarantine settings ...
Страница 254: ...254 Figure 6 15 Manual Processing page ...
Страница 258: ...258 Quarantine Thresholds Figure 6 17 Quarantine thresholds settings ...
Страница 364: ...364 B APPENDIX Variables in Warning Messages List of Variables 365 Outbreak Management Alert Variables 367 ...
Страница 392: ...392 Technical Support F Secure Online Support Resources 393 Web Club 395 Virus Descriptions on the Web 395 ...
Страница 397: ......














































