52
C365-5G-Mini User Manual CB-V1.1
www.comms365.com | 01234 865880 | [email protected]
•
Action:
If the traffic is the same, the system will handle traffic according to the Action
(accept, drop, reject, don’t track).
•
Extra argument:
Passes additional arguments, use with care!
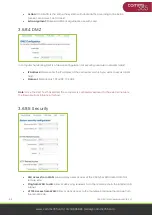
3.6.8.4 DMZ
In computer networking, DMZ is a firewall configuration for securing local area networks (LANs).
•
IP Address:
Please enter the IP address of the computer of which you want to set as a DMZ
host.
•
Protocol:
All protocols, TCP+UDP, TCP, UDP.
Note:
Once the DMZ host has settled, the computer is completely exposed to the external network;
the firewall will not influence this host.
3.6.8.5 Security
•
SSH access from WAN:
Allow or deny users access of the C365-5G-MINI router from THE
remote side.
•
Ping from WAN to LAN
: Allow or deny ping requests from the remote side to the internal LAN
subnet.
•
HTTPS access from WAN:
Allow or deny access to the router web management page from
the remote side.