Chapter 4: Operation of Web-based Management
724-746-5500 | blackbox.com
39
-----------------------------------------------------------------------
Rule 5: When both “accept and deny” lists exist, then it will deny all connections, excluding the connection within the acceptable range and
NOT within the denying range at the same time.
Accept
Deny
Deny| Acc | Deny | Acc | Deny
----------------------------------------------------------------------
Function name: Management Security Configuration
Function description: The switch offers Management Security Configuration. With this function, the manager can easily control the mode in
which the user connects to the switch. According to the mode, users can be classified into two types: Those who are able to connect to the
switch (Accept) and those who are unable to connect to the switch (Deny). You can place some restrictions on the user connect mode. For
example, you can decide which VLAN VID will be accepted or denied by the switch. You can also set the switch to accept or deny the users’
IP range, identify user ports that will connect to the switch, or control and connect to the switch via Http, Telnet or SNMP.
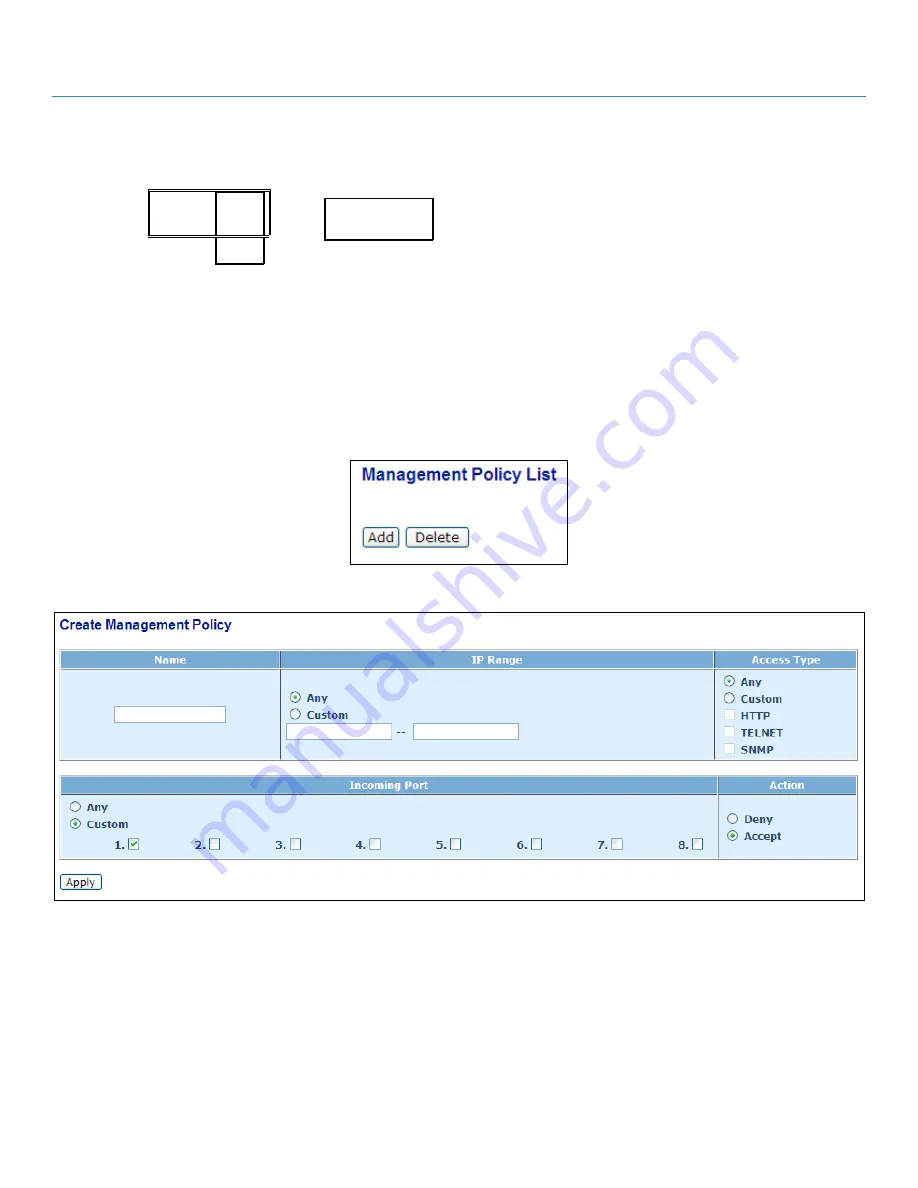
Figure 4-11. Management policy list screen.
Figure 4-12. Create management policy screen.
Parameter description:
Add: Press the <Add> button to create a new Management Security Configuration after you set up the parameters mentioned above. You
can also modify the existing entry by pressing this button.
Delete: Remove the existing Management Security Configuration entry from the management security table.
Name: A name can contain any letter (A–Z, a–z) and digit (0–9) with a maximum of 8 characters.
Accept
















































