19. Configuration Example: Policy
AirLive RS-2500 User’s Manual
156
19
19.
Configuration Example:
Policy Setting
19.1 Configuration Example (1) - Traffic Log, Statistic
Set up the policy that can monitor the internal users. (Take Traffic Log and Statistics for
example)
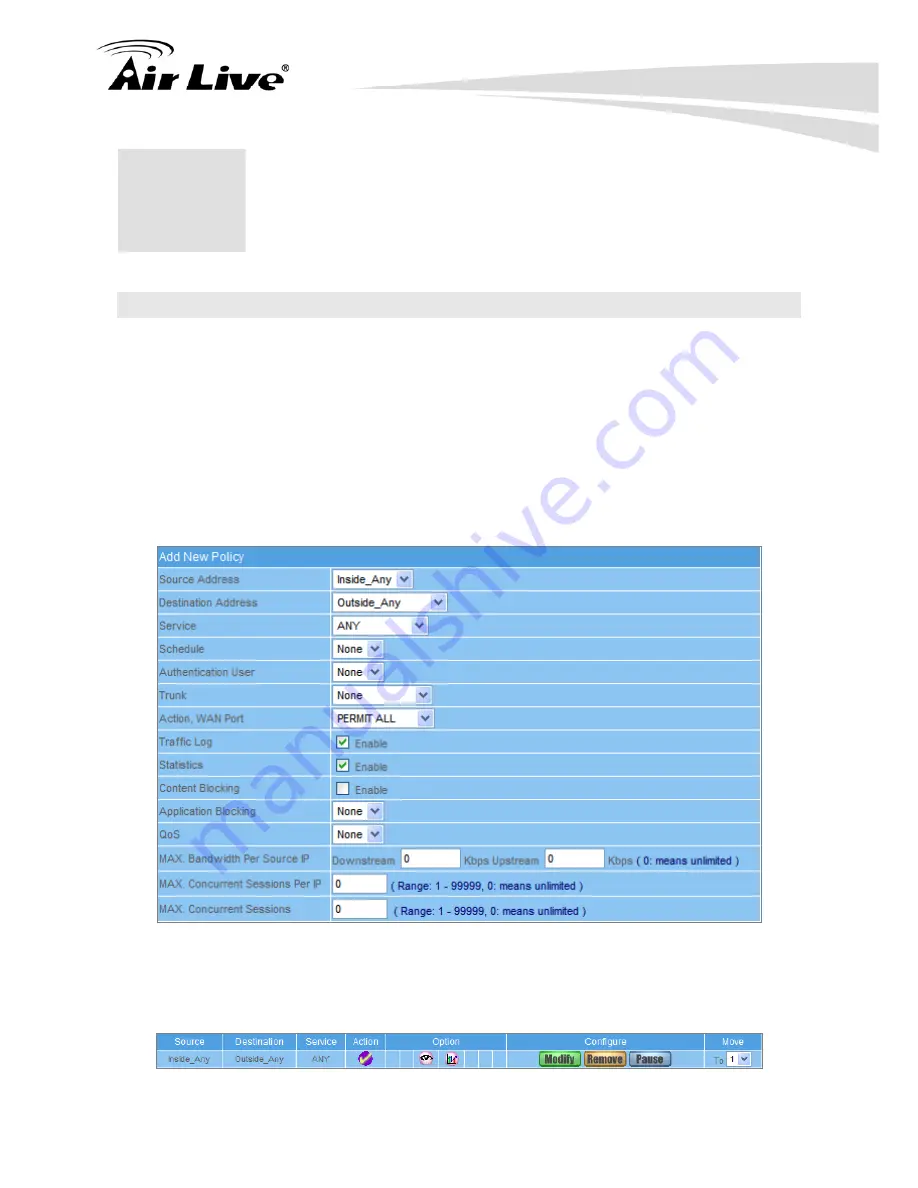
STEP 1
﹒
Enter the following setting in
Outgoing
Policy
:
Click
New Entry
Select
Traffic Log
Select
Statistics
Click
OK
(Figure 19-1)
Figure 19-1 Setting the different Policies
STEP 2
﹒
Complete the setting of Logging, Statistics, and Alarm Threshold in
Outgoing
Policy
: (Figure 19-2)
Figure 19-2 Complete Policy Setting
Содержание RS-2500
Страница 1: ...User s Manual Dual WAN Security VPN Gateway RS 2500 ...
Страница 218: ...22 Monitor 213 AirLive RS 2500 User s Manual Figure 22 23 To Detect WAN Statistics ...
Страница 220: ...22 Monitor 215 AirLive RS 2500 User s Manual Figure 22 25 To Detect Policy Statistics ...
Страница 224: ...22 Monitor 219 AirLive RS 2500 User s Manual Figure 22 30 Traceroute Results ...