27-18
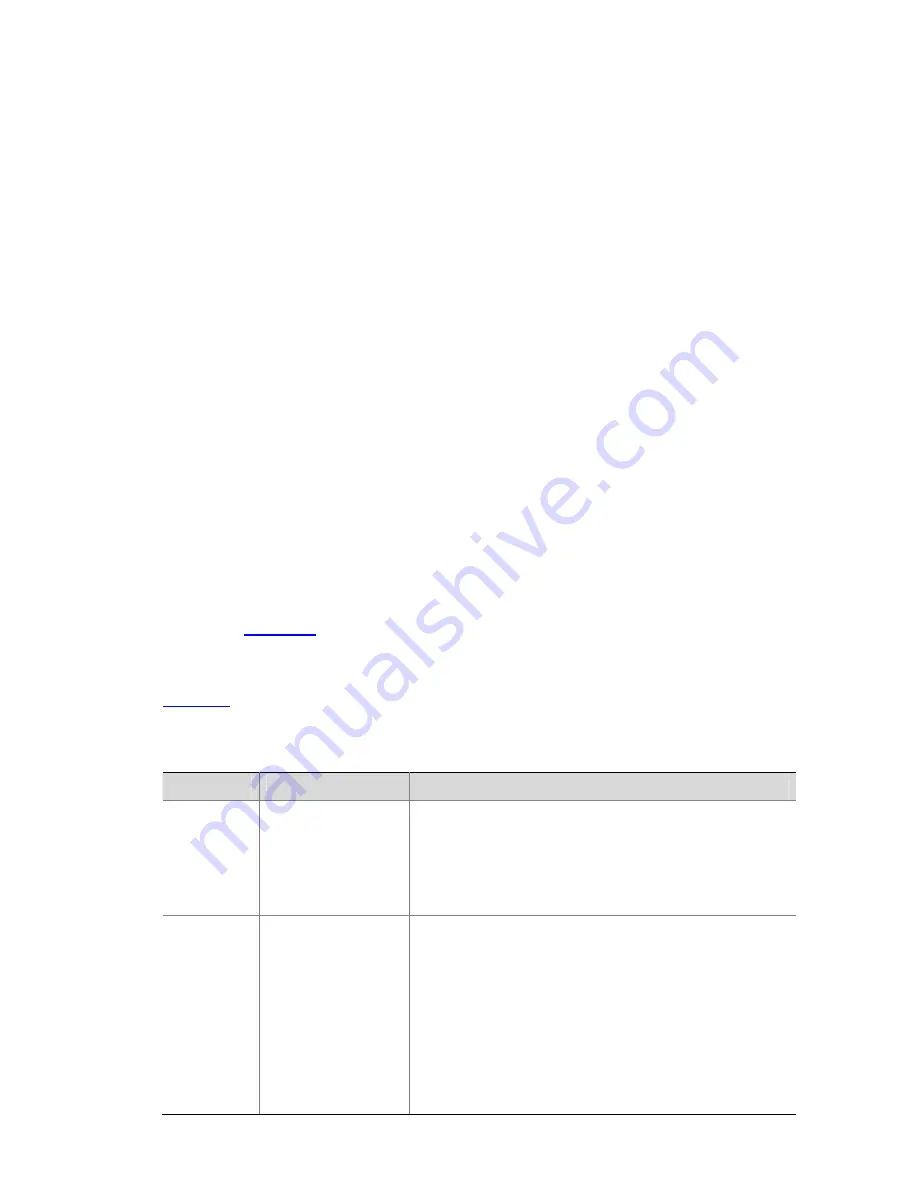
<SwitchA> display igmp-snooping group vlan100
Total 1 IP Group(s).
Total 1 MAC Group(s).
Vlan(id):100.
Total 1 IP Group(s).
Total 1 MAC Group(s).
Static Router port(s):
Dynamic Router port(s):
Ethernet1/0/1
IP group(s):the following ip group(s) match to one mac group.
IP group address: 224.1.1.1
Static host port(s):
Dynamic host port(s):
Ethernet1/0/3 Ethernet1/0/4
MAC group(s):
MAC group address: 0100-5e01-0101
Host port(s): Ethernet1/0/3 Ethernet1/0/4
As shown above, the multicast group 224.1.1.1 has been registered on Switch A, with the dynamic
router port Ethernet 1/0/1 and dynamic member ports Ethernet 1/0/3 and Ethernet 1/0/4. This means
that Host A and Host B have joined the multicast group 224.1.1.1.
Configuring Multicast VLAN
Network requirements
As shown in
Figure 27-4
, Workstation is a multicast source. Switch A forwards multicast data from the
multicast source. A Layer 2 switch, Switch B forwards the multicast data to the end users Host A and
Host B.
Table 27-2
describes the network devices involved in this example and the configurations you should
make on them.
Table 27-2
Network devices and their configurations
Device
Device description
Networking description
Switch A
Layer 3 switch
The interface IP address of VLAN 20 is 168.10.1.1. Ethernet
1/0/1 is connected to the workstation and belongs to VLAN
20.
The interface IP address of VLAN 10 is 168.10.2.1. Ethernet
1/0/10 belongs to VLAN 10. Ethernet 1/0/10 is connected to
Switch B.
Switch B
Layer 2 switch
z
VLAN 2 contains Ethernet 1/0/1 and VLAN 3 contains
Ethernet 1/0/2.
z
The default VLANs of Ethernet 1/0/1 and Ethernet 1/0/2
are VLAN 2 and VLAN 3 respectively.
z
VLAN 10 contains Ethernet 1/0/10, Ethernet 1/0/1, and
Ethernet 1/0/2. Ethernet 1/0/10 is connected to Switch A.
z
VLAN 10 is a multicast VLAN.
z
Ethernet 1/0/1 sends untagged packets for VLAN 2 and
VLAN 10.
z
Ethernet 1/0/2 sends untagged packets for VLAN 3 and
VLAN 10.






























