Chapter 37 MON Profile
UAG Series User’s Guide
433
37.3 Technical Reference
The following section contains additional technical information about the features described in this
chapter.
Rogue APs
Rogue APs are wireless access points operating in a network’s coverage area that are not under the
control of the network’s administrators, and can open up holes in a network’s security. Attackers
can take advantage of a rogue AP’s weaker (or non-existent) security to gain access to the network,
or set up their own rogue APs in order to capture information from wireless clients. If a scan reveals
a rogue AP, you can use commercially-available software to physically locate it.
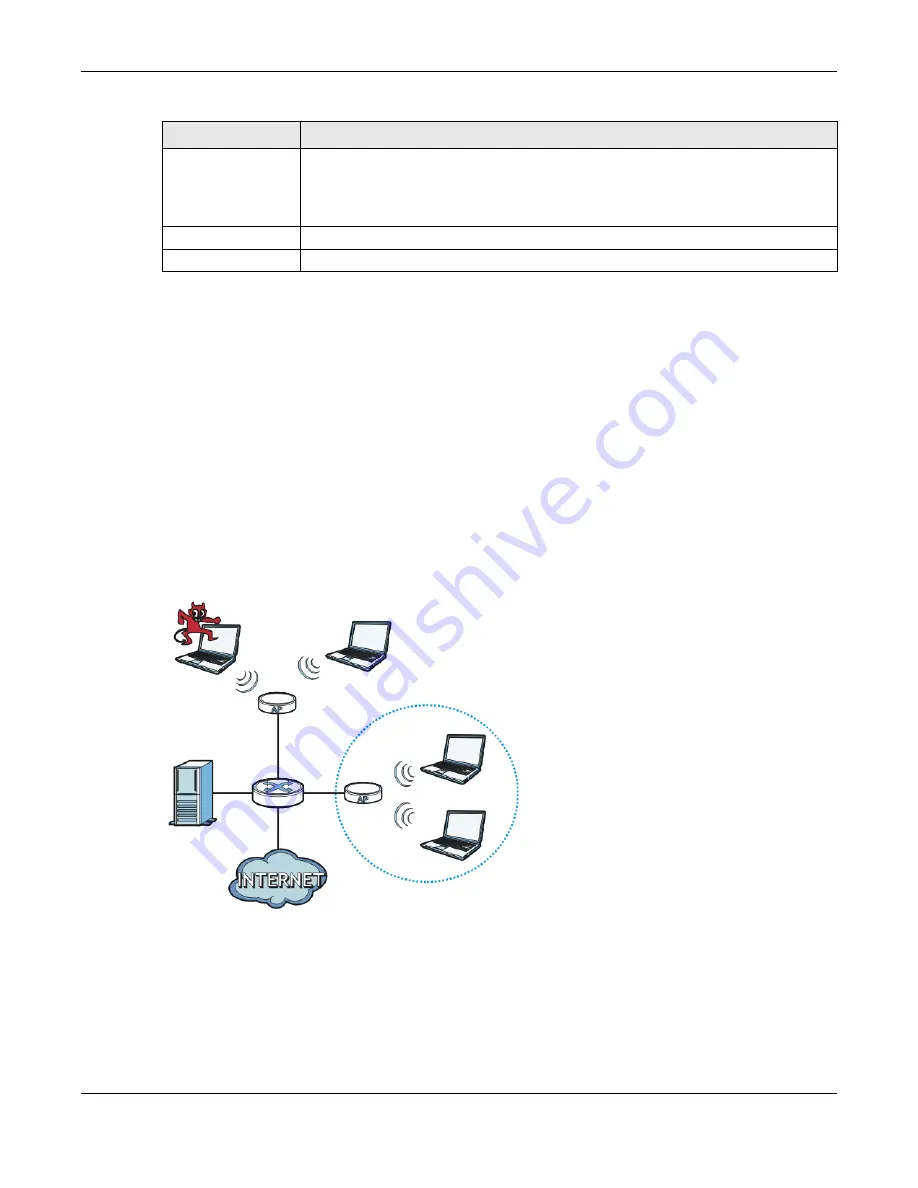
Figure 290
Rogue AP Example
In the example above, a corporate network’s security is compromised by a rogue AP (
RG
) set up by
an employee at his workstation in order to allow him to connect his notebook computer wirelessly
(
A
). The company’s legitimate wireless network (the dashed ellipse
B
) is well-secured, but the
rogue AP uses inferior security that is easily broken by an attacker (
X
) running readily available
encryption-cracking software. In this example, the attacker now has access to the company
network, including sensitive data stored on the file server (
C
).
Set Scan Channel
List (5 GHz)
Move a channel from the
Available channels
column to the
Channels selected
column to have the APs using this profile scan that channel when
Scan Channel Mode
is set to manual.
These channels are limited to the 5 GHz range (802.11 a/n).
OK
Click
OK
to
save your changes back to the UAG.
Cancel
Click
Cancel
to exit this screen without saving your changes.
Table 197
Configuration > Object > MON Profile > Add/Edit MON Profile (continued)
LABEL
DESCRIPTION
A
B
C
RG
X