Chapter 25 Security Policy
UAG Series User’s Guide
294
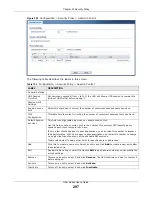
25.2.2 Add/Edit Policy Control Rule
In the
Policy Control
screen, click the
Add
icon or select a rule and click
Edit
to display this
screen.
Inactivate
To turn off an entry, select it and click
Inactivate
.
Move
To change a rule’s position in the numbered list, select the rule and click
Move
to display a
field to type a number for where you want to put that rule and press [ENTER] to move the
rule to the number that you typed.
The ordering of your rules is important as they are applied in order of their numbering.
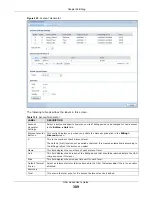
The following read-only fields summarize the policies you have created that apply to traffic traveling in the
selected packet direction.
Priority
This is the position of your security policy in the global policy list (including all through-UAG
and to-UAG policies). The ordering of your policies is important as policies are applied in
sequence.
Default
displays for the default security policy behavior that the UAG performs
on traffic that does not match any other security policy.
Status
This icon is lit when the entry is active and dimmed when the entry is inactive.
Name
This is the name of the security policy.
From
To
This is the direction of travel of packets to which the security policy applies.
Policy control rules are grouped based on the direction of travel of packets to which they
apply. For example, from
LAN
to
LAN
means packets traveling from a computer or subnet
on the LAN to either another computer or subnet on the LAN.
From
any
displays all the policy control rules for traffic going to the selected
To Zone
.
To
any
displays all the policy control rules for traffic coming from the selected
From Zone
.
From
any
to
any
displays all of the policy control rules.
To
Device
rules are for traffic that is destined for the UAG and control which computers can
manage the UAG.
IPv4 Source
This displays the IPv4 source address object to which this security policy applies.
IPv4 Destination This displays the IPv4 destination address object to which this security policy applies.
Service
This displays the service object to which this security policy applies.
User
This is the user name or user group name to which this security policy applies.
Schedule
This field tells you the schedule object that the policy uses.
none
means the policy is active
at all times if enabled.
Action
This field displays whether security policy silently discards packets (
deny
), or permits the
passage of packets (
allow
).
Log
This field shows you whether a log (and alert) is created when packets match this policy or
not.
UTM Profile
This field shows which UTM profiles (application patrol, content filter) apply to this policy.
Apply
Click
Apply
to save your changes back to the UAG.
Reset
Click
Reset
to return the screen to its last-saved settings.
Table 130
Configuration > Security Policy > Policy Control (continued)
LABEL
DESCRIPTION