DefensePro User Guide
Security Configuration
Document ID: RDWR-DP-V0602_UG1201
125
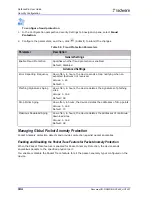
Configuring Early Blocking of DoS Traffic
Caution:
Modifying the values exposed in the Early Blocking of DoS Traffic feature may impair
the accuracy of the DoS-attack footprint that DefensePro generates.
When DefensePro detects a new DoS attack (by default, after 10 seconds), DefensePro generates a
DoS-attack footprint and then blocks or drops the relevant flood traffic.
In rare cases, such as very sensitive servers or firewalls, or in laboratory tests, it is required to start
blocking as soon as possible, even if accuracy is compromised. Using Early Blocking of DoS Traffic,
you can configure thresholds for generating DoS-attack footprints, which shorten the time to start
blocking the relevant traffic.
DefensePro generates each footprint using values from fields (parameters) in the packet header (for
example: Sequence Number, Checksum, and IP ID). The values from fields in the packet header
characterize the attack.
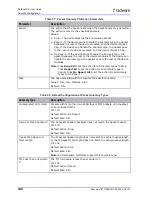
The thresholds that you can configure for the protection to change from the Analysis state to the
Blocking state are Packet-header fields or Packet-header-field values:
•
The Packet-header fields threshold is the anomalously distributed packet-header fields that
DefensePro must detect to generate a footprint and start early blocking prior to the default 10
seconds. (The transition after 10 seconds occurs even if the condition is not met.) You can define
either the number of packet-header fields, or the specific fields that DefensePro must detect. For
more information, see
Selecting Packet Header Fields for Early Blocking of DoS Traffic,
.
•
The Packet-header-field values threshold is the number of anomalous packet-header-field values
that DefensePro must detect to generate a footprint and start early blocking.
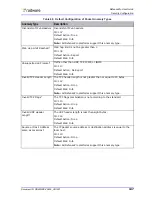
Note:
The threshold (that is, the packet-header fields or number of packet-header fields)
cannot conflict with the Footprint Strictness level. You cannot change the specified
Footprint Strictness to one that is lower than the strictness necessary for the BDoS
mechanism to operate properly. Likewise, you cannot configure fewer packet-header
fields than the specified strictness level requires for the BDoS mechanism to operate
properly.
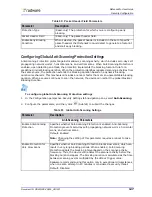
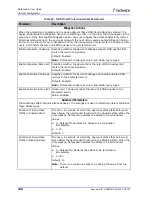
Bypass Status
The bypass option.
Values:
•
Bypass—The Behavioral DoS module bypasses all possible values of
the selected Bypass Field when generating a footprint.
•
Accept—The Behavioral DoS module bypasses only the specified
values (if such a value exists) of the selected Bypass Field when
generating a footprint.
Bypass Values
Used if the value of the Bypass Status parameter is Accept. Behavioral
DoS bypasses only the values of a selected Bypass Type, while it may use
all other values. These values vary according to the Bypass Field selected.
The values in the field must be comma-delimited.
Table 58: BDoS Footprint Bypass Parameters
Parameter
Description
Summary of Contents for DefensePro 6.02
Page 1: ...DefensePro User Guide Software Version 6 02 Document ID RDWR DP V0602_UG1201 January 2012 ...
Page 2: ...DefensePro User Guide 2 Document ID RDWR DP V0602_UG1201 ...
Page 20: ...DefensePro User Guide 20 Document ID RDWR DP V0602_UG1201 ...
Page 28: ...DefensePro User Guide Table of Contents 28 Document ID RDWR DP V0602_UG1201 ...
Page 116: ...DefensePro User Guide Device Network Configuration 116 Document ID RDWR DP V0602_UG1201 ...
Page 302: ...DefensePro User Guide Real Time Security Reporting 302 Document ID RDWR DP V0602_UG1201 ...
Page 308: ...DefensePro User Guide Administering DefensePro 308 Document ID RDWR DP V0602_UG1201 ...
Page 324: ...DefensePro User Guide Troubleshooting 324 Document ID RDWR DP V0602_UG1201 ...