QoS: Advanced
The QoS Advanced section is recommended for experienced users only. Please consult your
IT Provider if you have any uncertainty about these settings.
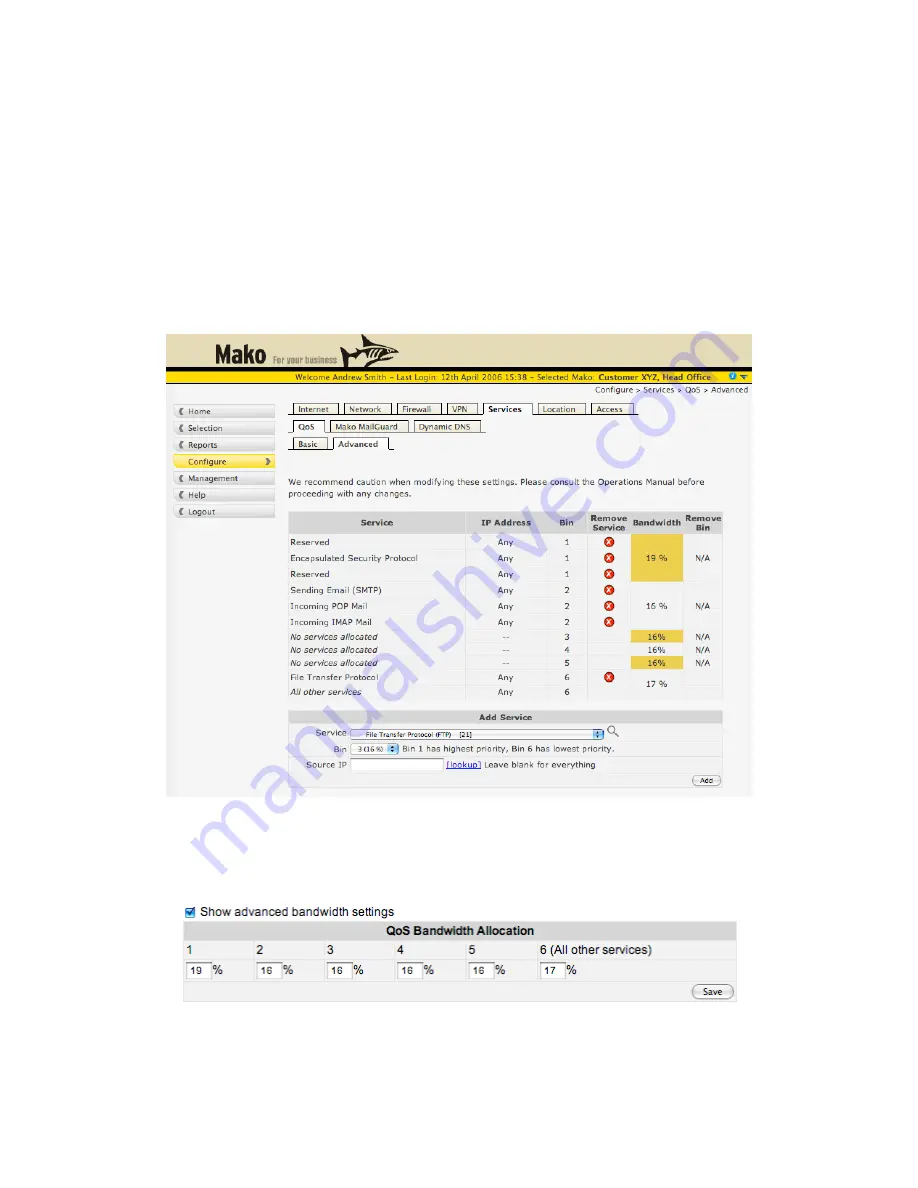
The upstream bandwidth is broken into 6 “Bins”. Bin 1 has higher priority than Bin 2 and Bin
2 has higher priority than Bin 3 and so on. You can group various Internet Services into
different Bins. All services that belong to a particular bin share its bandwidth. Important or
high priority services should be placed in a bin with no more than 2 other services to ensure
the bandwidth for the bin is not shared between too many services. All the services in a Bin
share that Bins allocation of bandwidth. The services are guaranteed that Bins percentage of
bandwidth as a minimum. If some upstream bandwidth is unused, it can be temporarily
borrowed from other bins until the bin needs the bandwidth.
Services that are not allocated to a bin use the last bin by default.
Quality of Service, Basic
By placing a tick in the Show advanced bandwidth settings box you can allocate upstream
bandwidth percentages across the Bins.
Advanced QoS Bandwidth Settings
Mako Networks Mako 7550-E Product Handbook v.1.1
Page 56















































