Page 70
Secure Connection
The browser and server use this information to negotiate a secure connection in the following manner:
The browser verifies the certificate authority’s authenticity by checking it against its own list of
CAs. (web browsers such as Microsoft Internet Explorer and Mozilla Firefox maintain data on
trusted CAs.)
After validating the CA, the browser and switch negotiate the highest level of security available to
both. The browser uses the public key to encrypt a random number and send it to the switch. The
switch uses a private key stored in memory (not advertised on the certificate) to decrypt it. From
this process, the browser and switch determine an algorithm for encrypting and decrypting all fur-
ther communication during the HTTPS session.
To enable secure HTTPS connections via SSL, the HTTPS Admin mode must be enabled on the
switch, and the web server must have a public key certificate. The switch can generate its own certifi-
cates, or you can generate these externally and upload them to the switch.
Certificates generated by the switch are
self-signed
; that is, the validity of the information provided
in the certificate is attested to by the switch itself.
Uploaded certificates can also be self-signed (by a server other than the switch), or they can be
root certificates
. A root certificate has been digitally signed by a CA, and is therefore considered to
provide a higher level of security.
You can also upload the encryption parameter files that provide algorithms for encrypting the key
exchanges.
To display the Secure HTTP Configuration page, click
Security
>
Secure Connection
in the naviga-
tion pane.
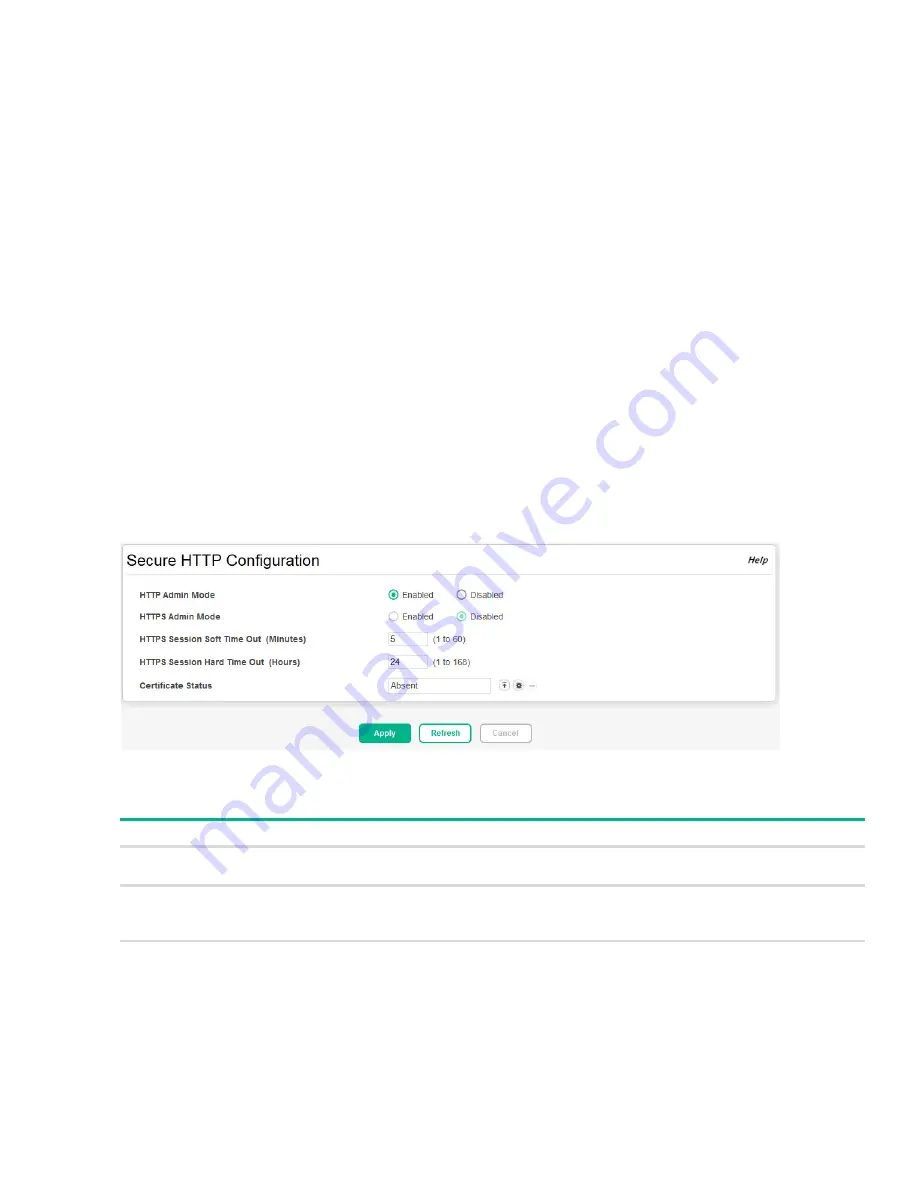
Figure 45. Secure HTTP Configuration
Table 37. Secure HTTP Configuration Fields
Field
Description
HTTP Admin Mode
Enable the Administrative mode of HTTP. This feature is enabled by default and can only be
disabled when the HTTPS Admin mode is enabled.
HTTPS Admin Mode
Enable to allow secure HTTPS sessions. When enabled, ensure that the Certificate Status
field reflects that a certificate is present. This feature is disabled by default.
Note that you can only upload SSL certificates when this mode is disabled.
HTTPS Session Soft Time
Out
The number of minutes after which an HTTPS session times-out if there is no user activity.
The default value is 5 minutes.
















































