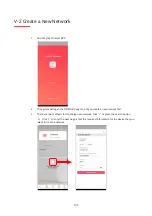
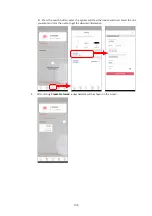
121
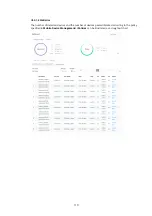
Item Description
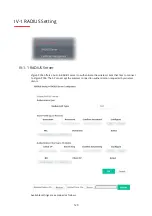
Enable RADIUS Server
Check it to enable the internal RADIUS server.
Authentication Type
Let the user choose the authentication method for the RADIUS server.
Radius EAP Type
– There are two types, PEAP and EAP TLS, offered
for selection. If EAP TLS is selected, a certificate must be installed or
must be ensured to be trusted.
Users Profile
Username
– Enter a new name for the user profile.
Password
– Enter a new password for this new user profile.
Confirm Password
– Retype the password to confirm it.
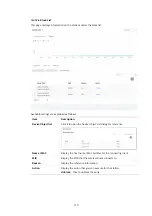
Configure
Add
– Make a new user profile with the name and password
specified on the left boxes.
Cancel
– Clear current settings for user profile.
Delete Selected
– Delete the selected user profile (s).
Delete All
– Delete all of the user profiles.
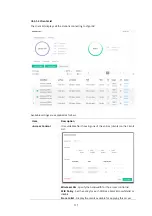
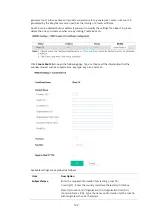
Authentication Client
This internal RADIUS server of VigorAP 906 can be treated as the
external RADIUS server for other users. Specify the client IP and secret
key to make the wireless client choosing VigorAP 906 as its external
RADIUS server.
Client IP
– Type the IP address for the user to be authenticated by
VigorAP 906 when the user tries to use VigorAP 906 as the external
RADIUS server.
Secret Key
– Type the password for the user to be authenticated by
VigorAP 906 while the user tries to use VigorAP 906 as the external
RADIUS server.
Confirm Secret Key
– Type the password again for confirmation.
Configure
Add
– Make a new client with IP and secret key specified on the
left boxes.
Cancel
– Clear current settings for the client.
Delete Selected
– Delete the selected client(s).
Delete All
– Delete all of the clients.
Backup Radius Cfg
Backup
- Click to store the configuration on this page as a file.
Upload From File
Browse
- Click to upload the RADIUS configuration file from the host
to VigorAP.
Restore
- Click to restore the RADIUS configuration file to VigorAP.
After finishing this web page configuration, please click
OK
to save the settings.
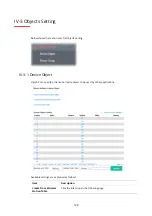
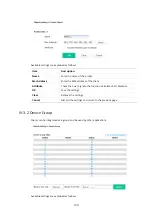
IV-1-2 Certificate Management
When the local client and remote server are required to make certificate authentication (e.g., Radius
EAP-TLS authentication) for wireless connection and avoiding the attack of MITM, a trusted root
certificate authority (Root CA) will be used to authenticate the digital certificates offered by both
ends.
However, the procedure of applying a digital certificate from a trusted root certificate authority is
complicated and time-consuming. Therefore, Vigor AP offers a mechanism that allows you to
Summary of Contents for VigorAP 906
Page 1: ...I ...
Page 7: ...VII Chapter I Installation ...
Page 8: ......
Page 18: ...10 Next click Change adapter options Click the local area connection ...
Page 28: ...20 4 A summary of the settings configuration will be shown on the screen Click Finish ...
Page 33: ...25 8 Later a summary page of mesh root with mesh node will be shown on the screen ...
Page 35: ...27 Chapter II Connectivity ...
Page 39: ...31 ...
Page 62: ...54 Below shows how Band Steering works ...
Page 66: ...58 ...
Page 82: ...74 Collect some Mesh logs and send the result to DrayTek for analysis ...
Page 84: ...76 II 4 7 Mesh Syslog ...
Page 95: ...87 Chapter III Management ...
Page 116: ...108 ...
Page 127: ...119 Chapter IV Others ...
Page 140: ...132 This page is left blank ...
Page 141: ...133 Chapter V Mobile APP DrayTek Wireless ...
Page 157: ...149 Chapter VI Troubleshooting ...
Page 161: ...153 VI 1 4 WLAN 2 4GHz Statistics This page is used for debugging by RD only ...
Page 169: ...161 ...