110
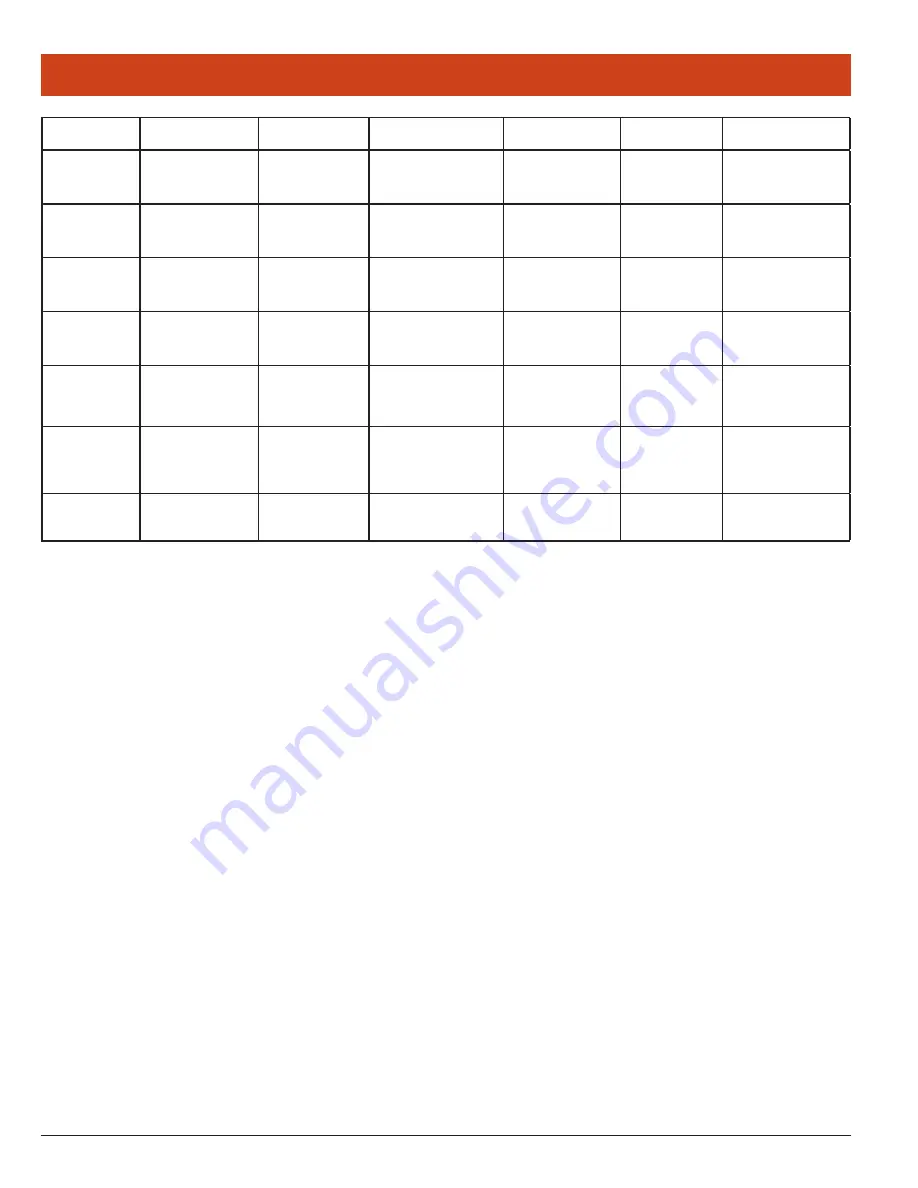
EAP-Type
User
Password
CA Cert
Validate
Server
User MS Store
Others
PEAP-MSCHAP
Username or Domain/
Username (up to 64
characters)
Password (up to 32
characters)
Filename (up to 32 char
-
acters)
See Note on CA Cert Field
See Note on Validate
Server Checkbox
See Note on Use
MS store Checkbox
PEAP-TGC
Username or Domain/
Username (up to 64
characters)
Password (up to 32
characters)
Filename (up to 32 char
-
acters)
See Note on CA Cert Field
See Note on Validate
Server Checkbox
See Note on Use
MS store Checkbox
PEAP-TLS
Username or Domain/
Username (up to 64
characters)
Password (up to 32
characters)
Filename (up to 32 char
-
acters)
See Note on CA Cert Field
See Note on Validate
Server Checkbox
See Note on Use
MS store Checkbox
EAP-TTLS
Username or Domain/
Username (up to 64
characters)
Password (up to 32
characters)
Filename (up to 32 char
-
acters)
See Note on CA Cert Field
See Note on Validate
Server Checkbox
See Note on Use
MS store Checkbox
EAP-TLS
Username or Domain/
Username (up to 64
characters)
Filename (up to 32 char
-
acters)
See Note on CA Cert Field
See Note on Validate
Server Checkbox
See Note on Use
MS store Checkbox
User Cert
See Note on User Cert
EAP-FAST
Username or Domain/
Username (up to 64
characters)
Password (up to 32
characters)
• PAC Filename (up to
32 characters)
• PAC Password (up to
32 characters)
LEAP
Username or Domain/
Username (up to 64
characters)
Password (up to 32
characters)
Note on CA Cert Field:
This is the filename of the root certificate au-
thority digital certificate. Leave this blank if the Use MS Store checkbox
is checked.
Note on Validate Server Checkbox:
Check this if using a CA cer
-
tificate to validate an authentication server. When this is checked, a cer-
tificate filename must be entered in the CA Cert field or check the Use
MS store checkbox.
Note:
Summit strongly recommends the use of server validation with
PEAP-GTC.
Note on Use MS Store Checkbox:
Check this if the Microsoft cer-
tificate store should be used for a CA certificate. This is applicable only
when Validate Server is checked.
Note on User Cert:
Tap the “...” button to select a user (or station)
certificate from the Microsoft certificate store. Do not enter a filename;
the user certificate must reside in the Microsoft certificate store. When
browsing for a certificate, the pop-up box displays Issued By and Issued
To.
Of the seven EAP types supported by SCU, all but EAP-FAST and LEAP
rely upon information in digital certificates that are created by a cer
-
tificate authority (CA). To enable a station device to authenticate the
Notes for EAP Credentials
server, provide a root CA certificate and distribute it to that station. The
CA certificate can be stored in a unit’s Microsoft certificate store or in a
specified directory (see Certs Path for additional information regarding
a specified directory).
Note:
For EAP-TLS, the user must also generate a user certificate for
each station. The user certificate must be stored in the Micro-
soft certificate store on the station.
EAP-FAST relies upon strong shared-secret keys that are unique to
users (rather than digital certificates). These keys are called protected
access credentials (PACs) and can be created automatically or manu
-
ally. With automatic or in-band provisioning, the PAC is created and
distributed to the station device in one operation. With manual or out-
of-band provisioning, the PAC is created in one step and must then be
distributed to the station device separately.
SCU supports PACs created automatically or manually. When the user
creates a PAC manually, it must be loaded into the directory identified
by the Certs Path global setting. Be sure that the PAC file does not have
read-only permissions set, or SCU will not be able to use the PAC.
Note:
If the user enter a PAC filename in the SCU field, manual pro
-
visioning is used. If the user omits the PAC filename, automatic
provisioning is used.
Appendix A — EAP Credentials



































