DRO-210i Web Configuration
DRO-210i User Manual Page 3-5
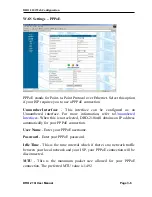
WAN Settings - Dynamic
Select this option if your ISP provides you an IP address automatically.
Dynamic IP address allows the DRO-210i to get its IP address information
from your ISP using the Dynamic Host Configuration Protocol (DHCP).
Use this setting if your ISP instructs you to use DHCP to automatically
obtain an IP address. A server on your ISP's network will then
automatically send the necessary IP address information to your router