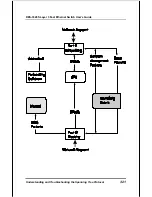
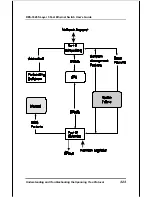
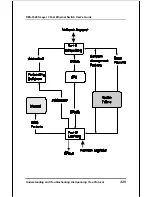
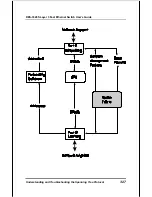
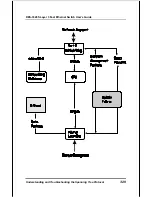
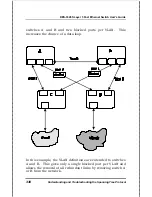
Reviews:
No comments
Related manuals for DES-3326S - Switch - Stackable

RBS Series
Brand: tbs electronics Pages: 2

MTX200
Brand: Aethra Pages: 1

MIC2042
Brand: Micrel Pages: 15

9109011003
Brand: Nobile Pages: 2

ITS 3000
Brand: E&C Pages: 10

SICOM3028GP Series
Brand: KYLAND Technology Pages: 40

pro-trim PT1000
Brand: Seastar Solutions Pages: 2

Master View CS-74A
Brand: ATEN Pages: 16

15-316
Brand: Radio Shack Pages: 8

JTECH-BS31
Brand: J-Tech Digital Pages: 12

3 x 4 SWITCH PLUS
Brand: W2IIHY Pages: 28

EXE 1512
Brand: Kathrein Pages: 41

Connect TS21
Brand: Marmitek Pages: 32

EG5-0702-SFP Series
Brand: Leonton Pages: 21

ICS5400PTP-12GT12GS4XS
Brand: 3onedata Pages: 3

GS305Pv2
Brand: NETGEAR Pages: 2

PM4X2
Brand: AAVARA Pages: 8

LCS-883R-SW8GD
Brand: Longshine Pages: 26