69
14.7 Configuration
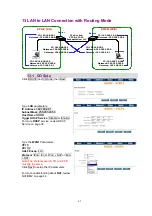
To setup the router, move the cursor “
>>
” to
enable
and press enter key. While the screen appears,
type the supervisor password. The default supervisor password is
root
. The password will be prompted
as “
*
“ symbol for system security.
----------------------------------------------------------------------
Command: enable <CR>
Message: Please input the following information.
Supervisor password:
****
----------------------------------------------------------------------
In this sub menu, you can setup management features and upgrade software, backup the system
configuration and restore the system configuration via utility tools.
For any changes of configuration, you have to write the new configuration to EPROM and reboot the
router to work with new setting.
The screen will prompt as follow.
>> enable
Modify command privilege
setup
Configure
system
status
Show running system status
show
View system configuration
write
Update flash configuration
reboot
Reset and boot system
ping
Packet internet groper command
admin
Setup management features
utility
TFTP upgrade utility
exit
Quit
system
Command Description:
Command Description
enable
Modify command privilege. When you login via serial console or Telnet, the
router defaults to a program execution (read-only) privileges to you. To change
the configuration and write changes to nonvolatile RAM (NVRAM), you must
work in enable mode.
setup
To configure the product, you have to use the setup command.
status
View the status of product.
show
Show the system and configuration of product.
write
Update flash configuration. After you have completed all necessary setting,
make sure to write the new configuration to NVRAM by “
write
” command and
reboot the system, or all of your changes will not take effect.
reboot
Reset and boot system. After you have completed all necessary setting, make
sure to write the new configuration to NVRAM and reboot the system by
“
reboot
” command, or all of your changes will not take effect.
ping
Packet internet groper command.
admin
You can setup management features in this command.
utility
Upgrade software and backup and restore configuration are working via “
utility
”
command.
exit
Quit system
Summary of Contents for SHDTU03b
Page 1: ...USER MANUAL SHDTU03b G SHDSL bis Bridge Router Modems CTC Union Technologies Co Ltd ...
Page 2: ......
Page 8: ......
Page 95: ......