©2015 Cradlepoint. All Rights Reserved.
|
+1.855.813.3385
|
cradlepoint.com
80
User Manual
/
AER3100/AER3150
THREAT MANAGEMENT
NOTE
: Threat Management is only available for the AER family or Cradlepoint products, and requires a feature
license. Enable this feature through
Enterprise Cloud Manager
.
Cradlepoint Secure Threat Management
leverages
Trend Micro
’s security experience and expertise in this
one-pass
Deep Packet Inspection
(DPI) solution.
Threat Management
includes settings for both IPS (
intrusion
prevention system
) and IDS (
intrusion detection system
), as well as application identification logging. Use
Threat Management
to identify and prevent a wide variety of network threats.
This
Threat Management
solution examines network traffic for both signature matches from Trend Micro’s large
signature database of known threats and statistical anomalies to detect previously unknown threats. Trend
Micro regularly adds new signatures to its database: update your signature database version to ensure you’re
defending yourself against the newest threats. You have the option to update manually or schedule regular
updates.
Follow these steps to get started with
Threat Management
:
1. To purchase a license or to begin a free trial, log into
Enterprise Cloud Manager
(ECM) and go to the
Applications
tab (this is only available to the primary account administrator). Once entitled, the router must
be rebooted for
Threat Management
to begin working.
2. Set up emailed or logged alerts in the
Alerts
tab in ECM.
3. Set up regularly scheduled signature updates in the configuration pages, or update manually in ECM via the
Devices
or
Groups
page (click on
Commands
in the top toolbar and select
Update IPS Signatures
from the
dropdown options).
NOTE
: Updating the signature database version causes a network disruption for a few seconds. You can schedule
these updates to occur during days/times when you expect less traffic on your network.
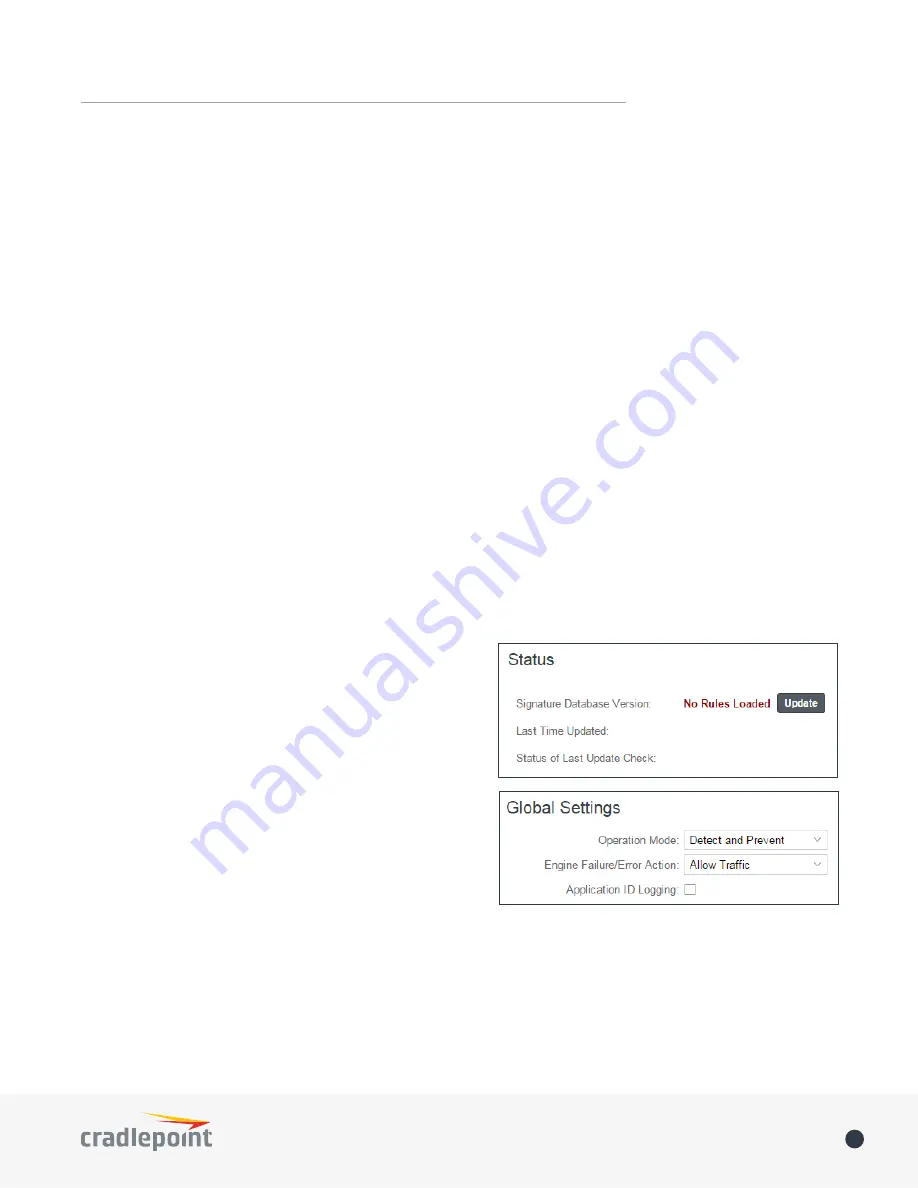
Status
The
Status
section shows if
Threat Management
is enabled.
It shows the current signature database version number, the
timestamp for the most recent update, and the status of the
most recent attempt to update signatures.
Click on the
Update
button to check for a new signature
database version.
Global Settings
Customize your
Threat Management
implementation (choose
between IPS and IDS, set up a signature update schedule,
etc.).
Operation Mode
: Choose
IPS
,
IDS
, or neither.
•
Disabled
•
Detect and Prevent
(default) –
IPS
mode
•
Detect Only
–
IDS
mode
In both
Detect and Prevent
and
Detect Only
modes, detected packets are logged to the System Log as well as
sent to your ECM account.
Engine Failure/Error Action
: In the unlikely event of an error with the
Threat Management
engine, you have the
following options:






























