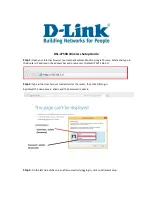
47
IPSec Proposal index
A list of selected proposal indexes from the IPSec proposal pool listed below. Selecting a proposal ID
and clicking «add to» button in the bottom of the page performs the selecting activity. There are
only four indexes can be chosen for the dedicated tunnel. Remove button beside the index list can
remove selected proposal index before.
Proposal name
It indicates which IPSec proposal to be focused. First char of the name
with 0x00 value
stands for
the proposal is not available.
DH group
There is three groups that can be selected: group 1 (MODP768), group 2 (MODP1024), group 5
(MODP1536). But none also can be selected here for IPSec proposal.
Encapsulation protocol
There are two protocols can be selected: ESP and AH.
Encryption algorithm
There is two algorithms that can be selected: 3DES and DES. But when the encapsulation protocol is
AH, encryption algorithm is unnecessarily set.
Authentication algorithm
There are two algorithms can be selected: SHA1 and MD5. But none also can be selected here for
IPSec proposal.
Life time
The unit of life time is based on the value of Life Time Unit. If the value of unit is second, the value
of life time represents the life time of dedicated VPN tunnel between both end gateways. Its value
ranges from 300 seconds to 172,800 seconds. If the value of unit is KB, the value of life time
Summary of Contents for WRM54
Page 17: ...17 4 4 Basic Setting 4 4 1 Primary Setup WAN Type Press Change...
Page 23: ...23 4 4 1 5 PPP over ATM RFC 2364 Press More...
Page 33: ...33 4 6 Security Settings 4 6 1 Packet Filter...
Page 50: ...50 4 7 Advanced Settings 4 7 1 System Time...
Page 61: ...61 4 8 Toolbox 4 8 1 System Log You can View system log by clicking the View Log button...
Page 71: ...71 7 Apply your settings...
Page 73: ...73 1 Start from the Red Hat System Setting Printing 2 Click Add Forward...
Page 74: ...74 3 Enter the Pinter Name Comments then forward 4 Select LPD protocol and then forward...
Page 84: ...84 Double click Administrative Tools...
Page 85: ...85 Local Security Policy Settings Double click Local Security Policy...
Page 88: ...88 click Add button...
Page 89: ...89 Enter a name for example xp router and deselect Use Add Wizard check box Click Add button...
Page 91: ...91 Click OK button Then click OK button on the IP Filter List page...
Page 95: ...95 select Authentication Methods page click Add button...
Page 99: ...99 click Add button...
Page 100: ...100 Enter a name such as router xp and unselect Use Add Wizard check box Click Add button...
Page 102: ...102 Click OK button Then click OK button on IP Filter List window...
Page 103: ...103 select Filter Action tab select Require Security then click Edit button...
Page 104: ...104 select Negotiate security Select Session key Perfect Forward Secrecy PFS click Edit button...
Page 105: ...105 select Custom button...
Page 107: ...107 select Authentication Methods page click Add button...
Page 110: ...110 select All network connections...
Page 111: ...111 Configure IKE properties Select General Click Advanced...
Page 114: ...114 VPN Settings VPN Enable Max number of tunnels 2 ID 1 Tunnel Name 1 Method IKE Press More...
Page 121: ...121 Figure 2 Enable IEEE 802 1X access control...
Page 123: ...123 Figure 4 Certificate information on PC1 Figure 5 Authenticating...