59 Copyright © Acronis, Inc., 2000-2009
To delete a backup location, select the location and click
Delete
. This will delete all
archives stored in this location and redirect the associated computer/user’s backups to the
default backup location.
The default backup location cannot be deleted. If you try to do so, the program will clean
the default backup location and issue an appropriate message. To delete the location
completely, first reassign the default backup location by selecting
Specify Default
Settings -> Set backup location
.
Cleaning and deleting backup locations might be time-consuming operations, so you can
schedule them for the off-peak period.
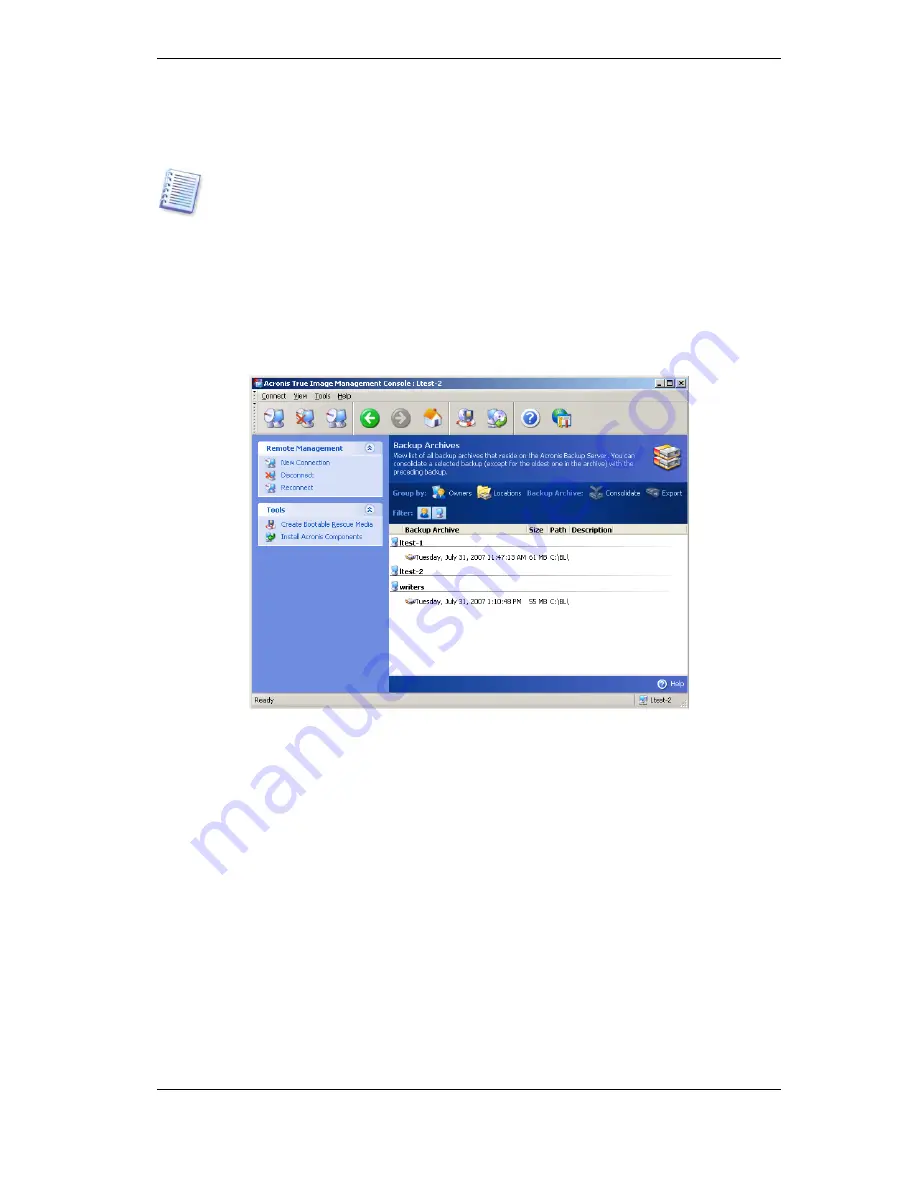
4.5.6 Managing Archives
To display a full list of backups, stored on the backup server, click
Manage Backup
Archives
.
You can:
1. Sort the list by
Location
or
Owners
(users and computers) by clicking on the
respective item above the list.
2. Filter out from the list all user’s or all computer’s backups (use buttons in the
Filter
group).
3.
Consolidate
any backup (except for the oldest one in the archive) with the preceding
backup file. This operation deletes the preceding backup and sets concatenation between
the backup being consolidated and the backup before the deleted one. Thus, the archive
integrity will not be affected, in spite of the fact that one backup will be deleted. Data
recovery from any of the remaining backups will be possible.
4. Export an archive from Acronis Backup Server to a local hard drive or network share.
To do so, select any backup belonging to the archive and click
Export
. Then provide
name for the archive copy and a path to the location where the copy will be created.
5. Import an archive from external location to a computer’s or user’s backup location on
the backup server. To do so, use
Import
on the toolbar.






























