Stephen Technologies Co.,Limited
www.stephen-tele.com
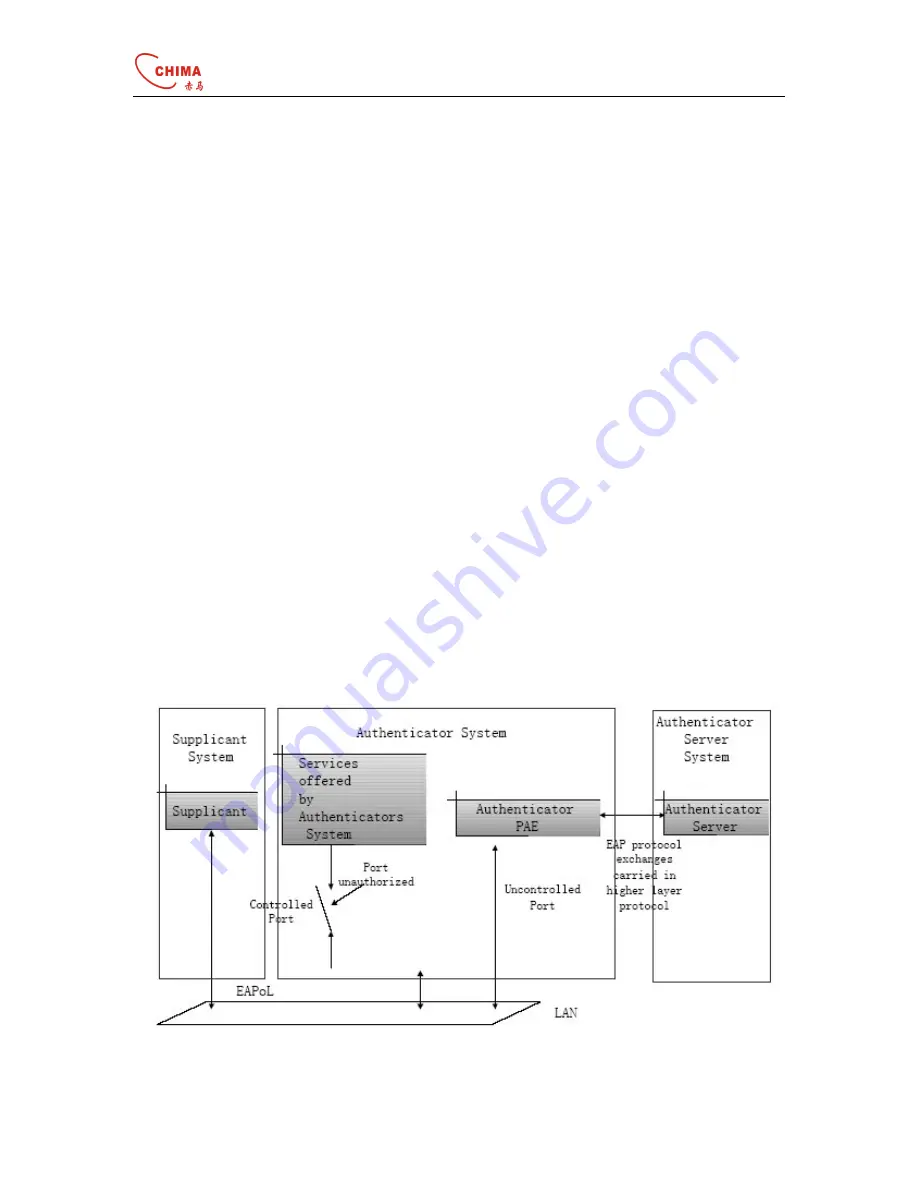
11.1.2 802.1x System Architecture
The system using the 802.1x is the typical C/S (Client/Server) system architecture. It contains
three entities, which are illustrated in the following figure: Supplicant System,Authenticator
System and Authentication Sever System.
The LAN access control device needs to provide the Authenticator System of 802.1x.The
devices at the user side such as the computers need to be installed with the 802.1x client
Supplicant software, for example, the 802.1x client provided by CHIMA (or by Microsoft
Windows XP). The 802.1x Authentication Sever system normally stays in the carrier’s AAA
center.
Authenticator and Authentication Sever exchange information through EAP (Extensible
Authentication Protocol) frames. The Supplicant and the Authenticator exchange information
through the EAPoL (Extensible Authentication Protocol over LANs) frame defined by IEEE
802.1x. Authentication data are encapsulated in the EAP frame, which is to be encapsulated
in the packets of other AAA upper layer protocols (e.g. RADIUS) so as to go through the
complicated network to reach the Authentication Server. Such procedure is called EAP Relay.
There are two types of ports for the Authenticator. One is the Uncontrolled Port, and the other
is the Controlled Port. The Uncontrolled Port is always in bi-directional connection state. The
user can access and share the network resources any time through the ports.The Controlled
Port will be in connecting state only after the user passes the authentication. Then the user is
allowed to access the network resources.
Figure 11-1
802.1x system architecture






























