5-39
Configuring the RADIUS Server—Without Identity Driven Manager
Configure the NAC 800 as a RADIUS Server
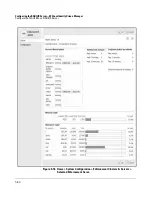
Figure 5-17. Home > System Configuration > Enforcement Clusters & Servers
2.
Click the name of the CS or ES. The
Enforcement server
window is dis-
played.
N o t e
Figure 5-18 shows the
Enforcement server
window for a CS. The window for an
ES features two menu options:
General
and
Configuration
. You should select
the
General
menu option.
Содержание 800
Страница 1: ...Configuration Guide www procurve com ProCurve Network Access Controller 800 ...
Страница 2: ......
Страница 3: ...ProCurve Network Access Controller 800 Configuration Guide April 2008 1 0 30398 ...
Страница 74: ...1 62 Overview of the ProCurve NAC 800 Deployment Methods ...
Страница 145: ...3 17 Initial Setup of the ProCurve NAC 800 System Settings Figure 3 9 Home System Configuration Management Server ...
Страница 155: ...3 27 Initial Setup of the ProCurve NAC 800 System Settings ...
Страница 194: ...3 66 Initial Setup of the ProCurve NAC 800 Digital Certificates ...
Страница 328: ...5 64 Configuring the RADIUS Server Without Identity Driven Manager Manage Digital Certificates for RADIUS ...
Страница 336: ...6 8 Disabling Endpoint Integrity Testing Overview ...
Страница 354: ...7 18 Redundancy and Backup for RADIUS Services Back Up Your NAC 800 Configuration ...
Страница 380: ...A 26 Appendix A Glossary ...
Страница 394: ...B 14 Appendix B Linux Commands Service Commands ...
Страница 405: ......
Страница 406: ... Copyright 2007 2008 Hewlett Packard Development Company L P April 2008 Manual Part Number 5991 8618 ...