ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
8-24
Virtual Private Networking Using SSL Connections
v1.0, September 2009
4.
Click the
Add
table button. The new application entry is added to the List of Configured
Applications for Port Forwarding table. Remote users can now securely access network
applications once they have logged into the SSL VPN portal and launched port forwarding.
To delete an application from the List of Configured Applications for Port Forwarding table, select
the checkbox to the left of the application that you want to delete, and then click the
delete
table
button in the Action column.
Adding A New Host Name
After you have configured port forwarding by defining the IP addresses of the internal servers and
the port number for TCP applications that are available to remote users, you then can also specify
“host-name-to-IP-address-resolution” for the network servers as a convenience for users. Host
name resolution allows users to access TCP applications at familiar addresses such as
mail.example.com or ftp.customer.com rather than by IP addresses.
To add servers and host names for client name resolution:
1.
Select
VPN
>
SSL VPN
from the menu. The SSL VPN s submenu tabs appear, with the
Policies screen in view.
2.
Click the
Port Forwarding
submenu tab.
The Port Forwarding screen displays (see
Figure 8-14 on page 8-23
).
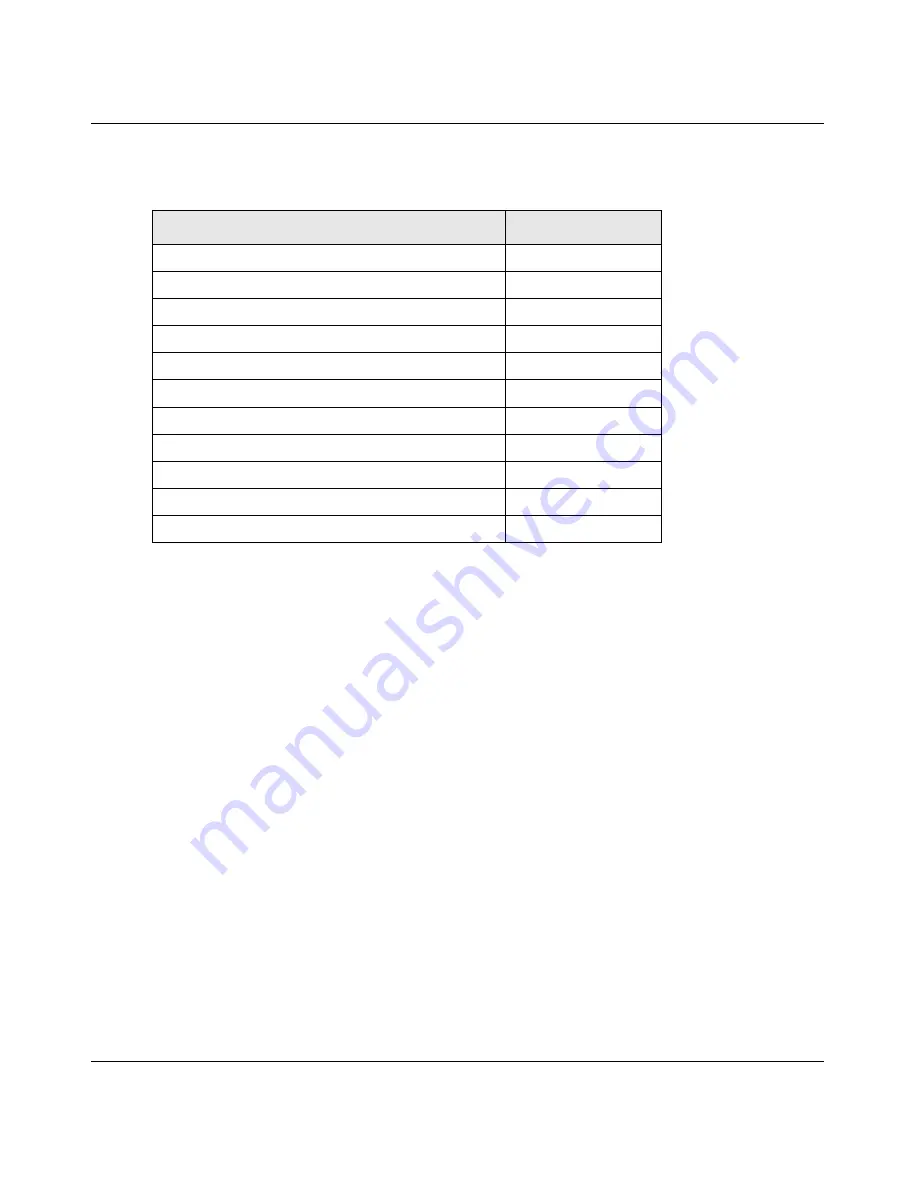
Table 8-7. Port Forwarding Applications/TCP Port Numbers
TCP Application
Port Number
FTP Data (usually not needed)
20
FTP Control Protocol
21
SSH
22
a
a. Users can specify the port number together with the host name or IP address.
Telnet
23
a
SMTP (send mail)
25
HTTP (web)
80
POP3 (receive mail)
110
NTP (network time protocol)
123
Citrix
1494
Terminal Services
3389
VNC (virtual network computing)
5900 or 5800
Содержание UTM10 - ProSecure Unified Threat Management Appliance
Страница 6: ...v1 0 September 2009 vi...
Страница 16: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual xvi v1 0 September 2009...
Страница 114: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual 4 28 LAN Configuration v1 0 September 2009...
Страница 464: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual E 2 Related Documents v1 0 September 2009...





































