ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
7-44
Virtual Private Networking Using IPsec Connections
v1.0, September 2009
.
4.
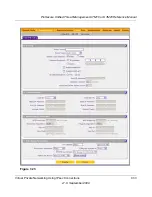
Complete the fields, select the checkbox, and make your selections from the pull-down menus
as explained
Table 7-15
.
Figure 7-26
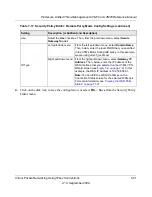
Table 7-15. Add Mode Config Record Settings
Item
Description (or Subfield and Description)
Client Pool
Record Name
A descriptive name of the Mode Config record for identification and
management purposes.
First Pool
Assign at least one range of IP pool addresses in the First Pool fields to enable
the UTM to allocate these to remote VPN clients. The Second Pool and Third
Pool fields are options. To specify any client pool, enter the starting IP address
for the pool in the Starting IP field and enter the ending IP address for the pool in
the Ending IP field.
Note
: Any IP pool should not be within the local network IP addresses. Use a
different range of private IP addresses such as 172.173.xxx.xx.
Second Pool
Third Pool
Содержание UTM10 - ProSecure Unified Threat Management Appliance
Страница 6: ...v1 0 September 2009 vi...
Страница 16: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual xvi v1 0 September 2009...
Страница 114: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual 4 28 LAN Configuration v1 0 September 2009...
Страница 464: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual E 2 Related Documents v1 0 September 2009...