ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
7-40
Virtual Private Networking Using IPsec Connections
v1.0, September 2009
server in the network when a user requests access to network resources. During the establishment
of a VPN connection, the VPN gateway can interrupt the process with an XAUTH request. At that
point, the remote user must provide authentication information such as a user name and password
or some encrypted response using his user name and password information. The gateway then
attempts to verify this information first against a local user database (if RADIUS-PAP is enabled)
and then by relaying the information to a central authentication server such as a RADIUS server.
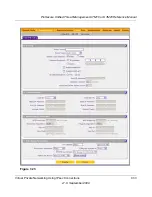
To configure primary and backup RADIUS servers:
1.
Select
VPN
>
IPSec VPN
from the menu. The IPsec VPN submenu tabs appear with the IKE
Policies screen in view.
2.
Click the
RADIUS Client
submenu tab.
The RADIUS Client screen displays.
Figure 7-24
Содержание UTM10 - ProSecure Unified Threat Management Appliance
Страница 6: ...v1 0 September 2009 vi...
Страница 16: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual xvi v1 0 September 2009...
Страница 114: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual 4 28 LAN Configuration v1 0 September 2009...
Страница 464: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual E 2 Related Documents v1 0 September 2009...