ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
Content Filtering and Optimizing Scans
6-39
v1.0, September 2009
4.
Click
Apply
to save your settings.
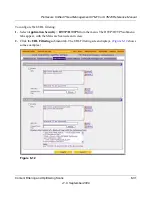
Configuring FTP Scans
Some malware threats are specifically developed to spread through the FTP protocol. By default,
the UTM scans FTP traffic, but you can specify how the UTM scans FTP traffic and which action
is taken when a malware threat is detected.
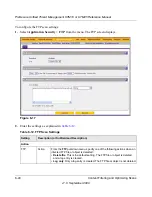
Hosts
This field contains the trusted hosts for which scanning is bypassed. To add a host to this
field, use the Add Host field or the Import from File tool (see below). You can add a
maximum of 200 URLs.
delete
To delete one or more hosts, highlight the hosts, and click the
delete
table
button.
export
To export the hosts, click the
export
table button and follow the instructions of
your browser.
Add Host
Type or copy a trusted host in the Add Host field. Then, click the
add
table button to add
the host to the Host field.
Import from
File
To import a list with trusted hosts into the Host field, click the
Browse
button and navigate
to a file in .txt format that contains line-delimited hosts (that is, one host per line). Then,
click the
upload
table button to add the hosts to the Host field.
Note
: Any existing hosts in the Host field are overwritten when you import a list of hosts
from a file.
Note:
The UTM does not scan password-protected FTP files.
Table 6-11. Trusted Hosts Settings (continued)
Setting
Description (or Subfield and Description)
Содержание UTM10 - ProSecure Unified Threat Management Appliance
Страница 6: ...v1 0 September 2009 vi...
Страница 16: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual xvi v1 0 September 2009...
Страница 114: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual 4 28 LAN Configuration v1 0 September 2009...
Страница 464: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual E 2 Related Documents v1 0 September 2009...