ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual
Virtual Private Networking Using IPsec Connections
7-37
v1.0, September 2009
5.
Click
Apply
to save your settings. The VPN policy is added to the List of VPN Policies table.
To edit a VPN policy:
1.
Select
VPN
>
IPSec VPN
from the menu. The IPsec VPN submenu tabs appear with the IKE
Policies screen in view.
2.
Click the
VPN Policies
submenu tab.
The VPN Policies screen displays (see
Figure 7-22 on
page 7-31
).
3.
In the List of VPN Policies table, click the
edit
table button to the right of the VPN policy that
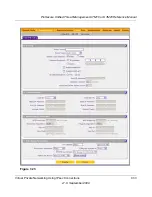
you want to edit. The Edit VPN Policy screen displays. This screen shows the same field as the
Add VPN Policy screen (see
Figure 7-23 on page 7-33
).
4.
Modify the settings that you wish to change (see
Table 7-12
).
5.
Click
Apply
to save your changes. The modified VPN policy is displayed in the List of VPN
Policies table.
Configuring Extended Authentication (XAUTH)
When many VPN clients connect to a UTM, you might want to use a unique user authentication
method beyond relying on a single common pre-shared key for all clients. Although you could
configure a unique VPN policy for each user, it is more efficient to authenticate users from a stored
list of user accounts. XAUTH provides the mechanism for requesting individual authentication
information from the user, and a local user database or an external authentication server, such as a
RADIUS server, provides a method for storing the authentication information centrally in the local
network.
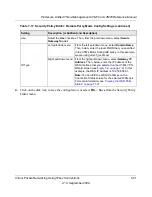
PFS Key Group
Select this checkbox to enable Perfect Forward Secrecy (PFS), and then
select a Diffie-Hellman (DH) group from the pull-down menu. The DH Group
sets the strength of the algorithm in bits. The higher the group, the more
secure the exchange. From the pull-down menu, select one of the following
three strengths:
•
Group 1 (768 bit)
.
•
Group 2 (1024 bit)
. This is the default setting.
•
Group 5 (1536 bit)
.
Select IKE Policy
Select an existing IKE policy that defines the characteristics of the Phase-1
negotiation. Click the
view selected
button to display the selected IKE
policy.
Table 7-12. Add VPN Policy Settings (continued)
Item
Description (or Subfield and Description)
Содержание UTM10 - ProSecure Unified Threat Management Appliance
Страница 6: ...v1 0 September 2009 vi...
Страница 16: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual xvi v1 0 September 2009...
Страница 114: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual 4 28 LAN Configuration v1 0 September 2009...
Страница 464: ...ProSecure Unified Threat Management UTM10 or UTM25 Reference Manual E 2 Related Documents v1 0 September 2009...