Protecting Your Wireless Network
B
SVG6x82 Series Wireless Voice Gateway
•
User Guide
20
590934-001-a
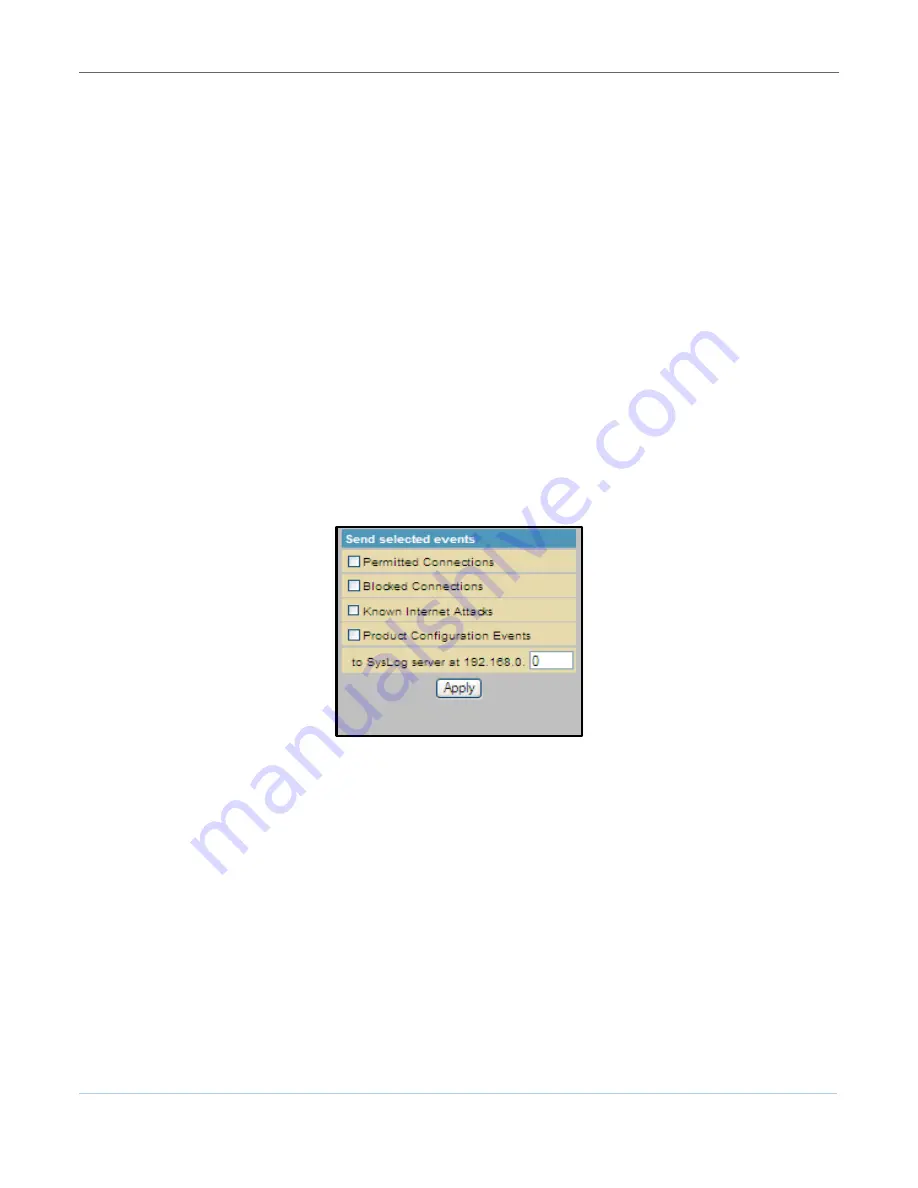
Firewall Remote Log
This Firewall configuration sends firewall attack reports to a standard SysLog server so that multiple
instances can be logged over a period of time. You can select individual attack or configuration items to
send to the SysLog server so that only the items of interest will be monitored. You can log any of the
following:
•
Permitted connections
- Select to have the server e-mail you logs of who is connecting to your
network.
•
Blocked connections
- Select to have the server e-mail you logs of who is blocked from connecting
to your network.
•
Known Internet attack types
- Select to have the server e-mail you logs of known Internet attacks
against your network.
•
Product configuration events
- Select to have the server e-mail you logs of the basic product
configuration events logs.
Note
: The SysLog server must be on the same network as the Private LAN behind the Configuration
Manager (typically
192.168.0.x
).
To open the Firewall Remote Log page:
1.
Click
Firewall
on the SVG6x82 Menu Options bar.
2.
Click
Remote Log
from the Status submenu options.
Figure 14 – Firewall Remote Log Page
3.
Select all the desired event types that you want to monitor.
4.
Enter the last byte (from
10
to
254
) of the IP address of the SysLog server.
Note
: Normally, the IP address of this SysLog server is hard-coded so that the address does not
change and always agrees with the entry on this page.
5.
Click
Apply.
























