58
Section 3: Configuring the Access Point
LAPAC1750PRO Access Point Software User Manual
The devices connected to the wired interface of the access point, as well as the
downstream stations associated to the access point’s access point interface can
access the network connected by the infrastructure client interface To allow
the bridging of packets, the VLAN configuration for the access point interface
and wired interface should match that of the infrastructure client interface
Workgroup Bridge mode can be used as range extender to enable the BSS to
provide access to remote or hard-to-reach networks A single-radio can be
configured to forward packets from associated STAs to another access point in
the same ESS, without using WDS
NOTE:
Workgroup Bridge mode currently supports only IPv4 traffic
NOTE:
Workgroup Bridge mode is not supported across a cluster
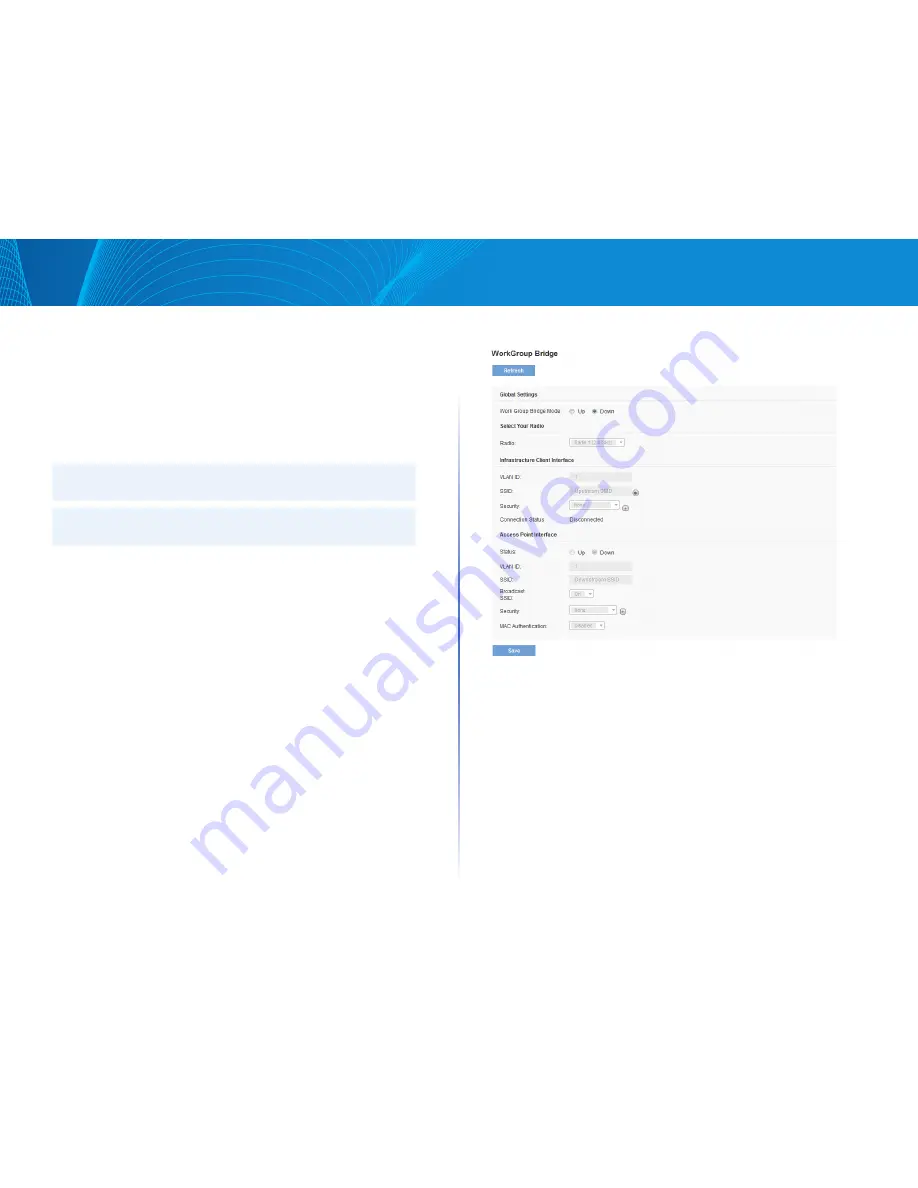
Use the WorkGroup Bridge page to configure the Work Group Bridge mode
on the AP and to configure the settings that allow the AP to serve as a bridge
between remote clients and the wireless LAN
To configure the Workgroup Bridge settings, click the
Configuration > Wireless
> WorkGroup Bridge
tab
Figure 33: Workgroup Bridge
Содержание LAPAC1750PRO
Страница 1: ...LAPAC1750PRO User Guide ...






























