SPYDER MODEL 5 ENGINEERING TOOL
–
USER GUIDE
31-00282ES-01
4
ABOUT THIS USER GUIDE
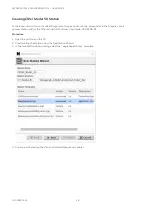
This user guide describes the configuration and management of Spyder Model 5 controllers connected to a BACnet
MSTP network via a CIPer Model 50 controller. Configuration and Management is done by using the Spyder Model 5
Engineering Tool based on the Honeywell WEBStation.
Applicable Technical Literature
•
Spyder Model 5 Product Data: 31-00280ES-01
•
Spyder Model 5 Installation Guide: 31-00281ES
•
IRM-NX FUNCTION BLOCKS User Guide: EN2B-0415GE51
•
IRM-NX APPLICATION Guide: EN2B-0416GE51
•
Honeywell General Security Best Practices
–
System Engineering Guide: 31-00129
•
CIPer Model 30 Hardening Guide: 31-00207EFS
•
CIPer Model 50 Product Datasheet: 31-00197
•
CIPer Model 50 Installation & Commissioning Instructions: 31-00233EFS
•
CIPer Model 50 Mounting Instructions: 31-00234EFS
•
CIPer Model 50 Controller User Guide: 31-00198
SYSTEM REQUIREMENTS
Niagara
:
Honeywell WEBStation N4.4.94.xx and higher
Firmware
:
IRMN4-IMG_V0.0.7.1.bin
Tools
:
Spyder5_Tool_1.0.0.37
DemoApplication
:
IRMN_H_0001_Ver_1.0.1.5
Firmware and Software
Downloads :
The firmware and the software can be downloaded from
Restrictions and Recommendations
For successful and seamless engineering, it is recommended to note the following internal system restrictions:
Number of BACnet Devices :
max. 64 devices per channel. Depending on performance needs of
the application and bus traffic it is recommended to keep the number
of devices below 64.
Controller Memory Usage
:
max. 80 % (recommended 70 %)
Function Blocks Usage
:
- max. 32 IRM folders overall
- max. 100 function blocks per folder
- max. 2000 function blocks overall
- max 1 wall module per device
Baud rate
:
9600 through max. 76800 (default = 38400)
Security Best Practices
This section provides the necessary information about the requirements for configuring and managing the security
when installing and maintaining a product or system.
Honeywell hereby expressly states that its controllers are not inherently protected against cyber-attacks from the
Internet and that they are therefore intended solely for use in private networks. However, even private networks can
still be subject to malicious cyber-attacks by skilled and equipped IT individuals and thus require protection.
Customers should therefore adopt the installation and security best practices guidelines for Honeywell BACnet
MS/TP-based products to mitigate the risk posed by such attacks.