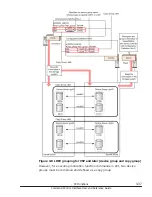
If multiple users (IDs) operate the same resource, you can prevent operation
conflict for the target resource by using the raidcom lock resource command
to confirm that no other user is using the resource.
After the configuration change is completed, release the lock status by the
raidcom unlock resource command.
The user who locks a resource is identified by the session information. When
the user logs out and the session information of the user is deleted from the
storage system, the resource that has been locked by the user is
automatically released. For details about the session information, see
.
Command execution modes
Overview
Provisioning operations are performed using a configuration setting
command. For details about the configuration setting command, see
Overview of the configuration setting command on page 5-2
Control Interface Command Reference.
Two modes can be used for executing the configuration setting command:
•
Line-by-line mode.
This mode executes commands input from the command line one at a
time.
•
Transaction mode.
Executes a script file specified by the -zt option.
When executing the configuration setting command, the following checks can
be done depending on the above two mode types.
•
Syntax check
This function checks if there is no syntax error in the specified command.
This is executed every time at the both line-by-line mode and transaction
mode.
•
Context check
This function checks the consistency of one specified line in the script and
the preceding lines in the order from the top. This function is available
only at the Transaction mode. For details about context checking, see
.
•
Configuration check
Acquire the current configuration information to a configuration file, and
then this function checks whether the resources specified in the script
(LDEVs, ports, or host groups) are configured in the storage system or
not. This function is available only at the transaction mode. For details
Configuration check on page 3-33
The configuration setting command also has a execution option described in
the following.
CCI functions
3-25
Command Control Interface User and Reference Guide
Содержание HUS VM
Страница 10: ...x Command Control Interface User and Reference Guide ...
Страница 18: ...xviii Preface Command Control Interface User and Reference Guide ...
Страница 78: ...2 50 CCI software environment Command Control Interface User and Reference Guide ...
Страница 154: ...4 8 Starting up CCI Command Control Interface User and Reference Guide ...
Страница 191: ...Provisioning operations with CCI 5 37 Command Control Interface User and Reference Guide ...
Страница 277: ... 1 UR 2x2 Data replication operations with CCI 6 53 Command Control Interface User and Reference Guide ...
Страница 280: ...6 56 Data replication operations with CCI Command Control Interface User and Reference Guide ...
Страница 286: ...6 62 Data replication operations with CCI Command Control Interface User and Reference Guide ...
Страница 302: ...7 16 Data protection operations with CCI Command Control Interface User and Reference Guide ...
Страница 324: ...8 22 Examples of using CCI commands Command Control Interface User and Reference Guide ...
Страница 524: ...9 200 Troubleshooting Command Control Interface User and Reference Guide ...
Страница 529: ...Command Control Interface User and Reference Guide ...