EOC-8610-S series 11a/b/g Wireless Multi-Client Bridge/AP/WDS
Version 2.2
-
26
-
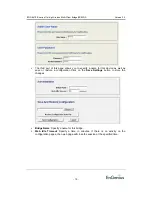
Channel
: Select a channel from the drop-down list. The channels available are
based on the country’s regulation. When selecting Infrastructure mode, a channel is
not required, however, when selecting Adhoc mode, you must select the same
channel on all points.
Transmission Rate
: Select a transmission rate from the drop-down list. It is
recommended to use the
Best (automatic)
option.
802.11 Mode
: Select
802.11b only
. Do not use this option when configured at Ad-
Hoc mode.
Setting ACK_G
Timeout:
You may specify a time out value, however, it is
recommended to use the default setting:
48
Click on the
Save Settings
button once you have modified the settings.
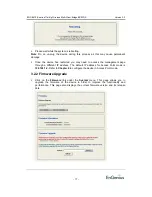
3.3.5 Wireless Security
Click on the
11a, 11b
,
or
11g
link under the
Wireless
menu. The third part of this
page allows you to configure the security settings of this device. To protect your
privacy this mode supports two types of wireless security: WEP and WPA-Personal.
WEP is the original wireless encryption standard. WPA provides a higher level of
security. WPA-Personal does not require an authentication server.
Select
the
None
radio button in order to disable security.
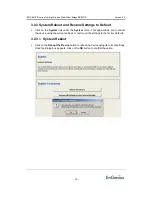
3.3.5.1.1
WEP (Wired Equivalent Privacy)
Select
the
WEP
radio button if your wireless network uses WEP encryption. WEP is
an acronym for Wired Equivalent Privacy, and is a security protocol that provides the
same level of security for wireless networks as for a wired network.
WEP is not as secure as WPA encryption. To gain access to a WEP network, you
must know the key. The key is a string of characters that you create. When using
WEP, you must determine the level of encryption. The type of encryption determines
the key length. 128-bit encryption requires a longer key than 64-bit encryption. Keys
are defined by entering in a string in HEX (hexadecimal - using characters 0-9, A-F)
or ASCII (American Standard Code for Information Interchange - alphanumeric
characters) format. ASCII format is provided so you can enter a string that is easier
to remember. The ASCII string is converted to HEX for use over the network. Four
keys can be defined so that you can change keys easily. A default key is selected for
use on the network.