DPtech FW1000 Series Firewall Products User Configuration Guide
8-214
7.4 SQL Injection Protection
SQL injection is a technique often used to attack databases through a website. SQL injection attack a website
through WWW normal port and it seems like the common webpage, firewall device cannot alarm for the SQL
injection and if an administrator does not view the IIS log, SQL injection for a long time will not detected, so that the
SQL injection protection is especially important.
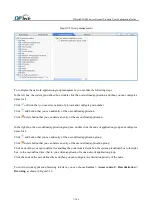
To enter the SQL injection protection interface, you can choose
Service > Access control > SQL injection
protection
, as shown in Figure7-18.
Figure7-18
SQL injection prevention
Table7-10 describes the configuration items of the SQL injection protection.
Table7-10
SQL injection protection configuration items
Item
Description
Name
Configure a name for the SQL injection protection rule.
Exceptional interface
Configure the exceptional interface.
Exceptional parameter
Configure the exceptional parameter
Action
Select an action for the rule, including warning and block
Operation
Click the
copy icon to copy an entry of the SQL injection protection rule.
Click the
delete icon to delete an entry of the SQL injection protection rule.
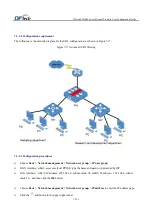
Chapter 8 VPN
A virtual private network (VPN) is a private network that interconnects remote (and often geographically separate)
networks through primarily public communication infrastructures such as the Internet. VPNs provide security
through tunneling protocols and security procedures such as encryption. For example, a VPN could be used to
securely connect the branch offices of an organization to a head office network through the public Internet.
IPSec