DES-6500 Chassis-based Layer 3 Ethernet Switch Manual
119
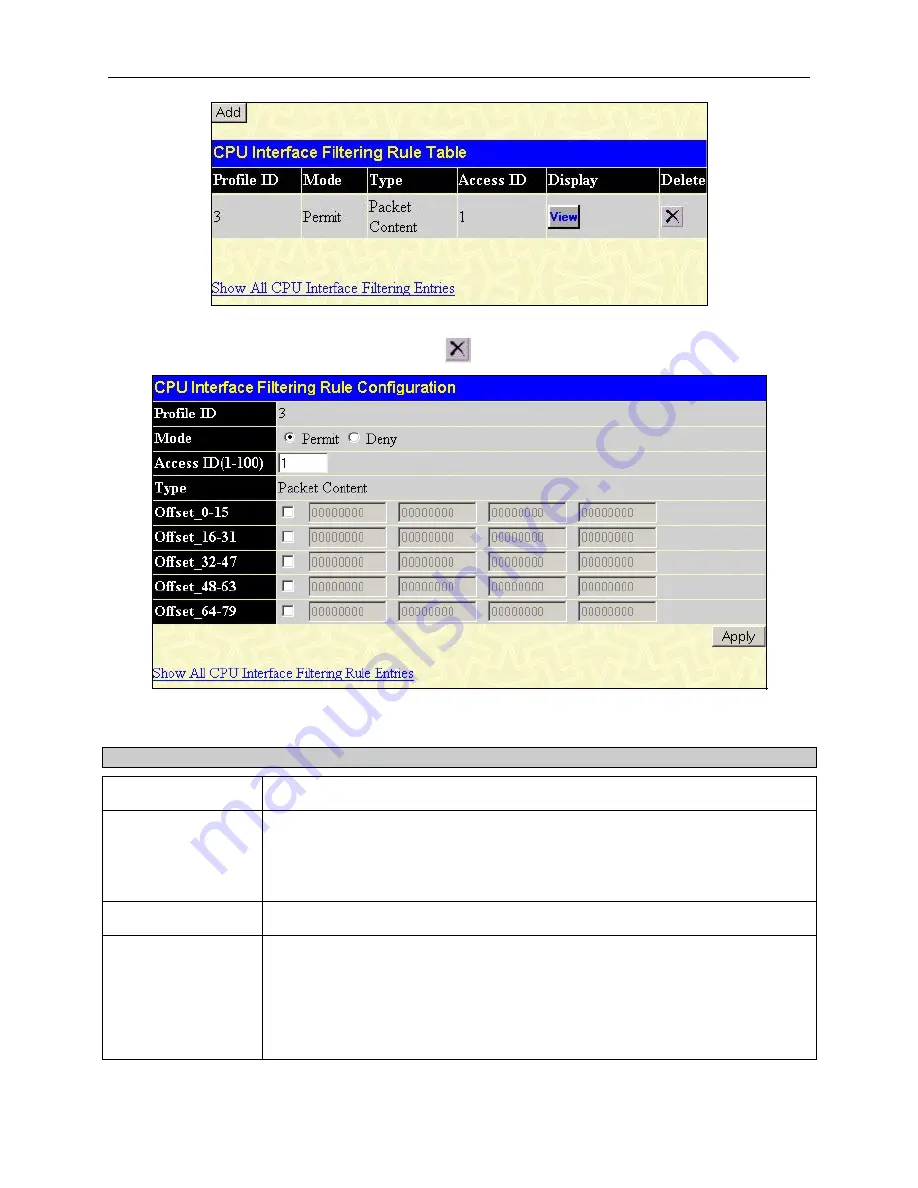
Figure 6- 80. CPU Interface Filtering Rule Table – Packet Content
To remove a previously created rule, select it and click the
button. To add a new Access Rule, click the
Add
button:
Figure 6- 81. CPU Interface Filtering Rule Configuration - Packet Content
To set the Access Rule for Ethernet, adjust the following parameters and click
Apply
.
Parameters Description
Profile ID
This is the identifier number for this profile set.
Mode
Select
Permit
to specify that the packets that match the access profile are forwarded
by the Switch, according to any additional rule added (see below).
Select
Deny
to specify that packets that do not match the access profile are not
forwarded by the Switch and will be filtered.
Access ID
Type in a unique identifier number for this access. This value can be set from 1 - 100.
Type
Selected profile based on Ethernet (MAC Address), IP address or Packet Content.
•
Ethernet
instructs the Switch to examine the layer 2 part of each packet
header.
•
IP
instructs the Switch to examine the IP address in each frame's header.
•
Packet Content Mask
instructs the Switch to examine the packet header.
Содержание TM DES-6500
Страница 1: ...D Link DES 6500 Modular Layer 3 Chassis based Ethernet Switch Firmware Release 2 5 Manual...
Страница 276: ...DES 6500 Chassis based Layer 3 Ethernet Switch Manual 275 Figure 10 8 Factory Reset to Default Value window...
Страница 331: ...330 D Link D Link D Link D Link 095 744 00 99 http www dlink ru email support dlink ru...
Страница 334: ...333...
Страница 349: ...348...
Страница 352: ...DES 6500 Stackable Gigabit Layer 3 Switch User Guide 351...






























