DIR-620S
Wireless N300 Router with 3G/LTE Support and
USB Port
User Manual
Configuring via Web-based Interface
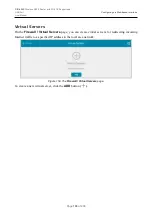
In the
Per-source IP Flood
section, you can enable protection against main types of DoS attacks.
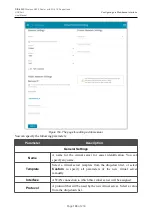
Parameter
Description
TCP/SYN
Enables protection against a flood with connection requests (TCP
packets with the SYN flag).
TCP/FIN
Enables protection against a flood with requests for connection
termination (TCP packets with the FIN flag).
UDP
Enables protection against a flood with UDP packets.
ICMP
Enables protection against a flood with ICMP packets.
Move the relevant switches to the right. In the
threshold
field corresponding to the switch, specify
the maximum number of packets which arrive from one IP address within one second. The value of
the field should be greater than zero (for example,
200
). Then, in the
Other Settings
section,
move the
Block source IP
switch to the right, and in the
Block time
field, specify the time
period (in seconds) during which the source IP address will be blocked. For example, you can
specify
120
. When the threshold value is exceeded, the source of packets will be blocked for the
specified time period.
In the
Other Settings
section, you can activate additional protection methods.
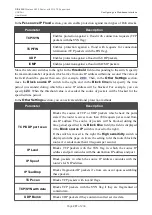
Parameter
Description
TCP/UDP port scan
Blocks the source of TCP or UDP packets which check the ports
state if the router receives more than 200 requests per second from
one IP address. The source of packets will be blocked during the
time period specified in the
Block time
field (the field is displayed
if the
Block source IP
switch is moved to the right).
If the switch is moved to the right, the
High sensitivity
switch is
displayed on the page. Activate the setting to let the router block the
source if it sends more than 10 requests per second.
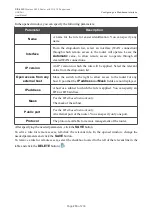
IP Land
Blocks TCP packets with the SYN flag in which the source IP
address and port coincides with the destination IP address and port.
IP Spoof
Block packets in which the source IP address coincides with the
router's LAN IP address.
IP TearDrop
Blocks fragmented IP packets if errors can occur upon assembling
these packets.
TCP scan
Blocks TCP packets with invalid flags.
TCP/SYN with data
Blocks TCP packets with the SYN flag if they are fragmented or
contain data.
UDP Bomb
Blocks UDP packets if they contain incorrect service data.
Page
207
of 236