xStack
®
DGS-3200 Series Layer 2 Gigabit Ethernet Managed Switch
116
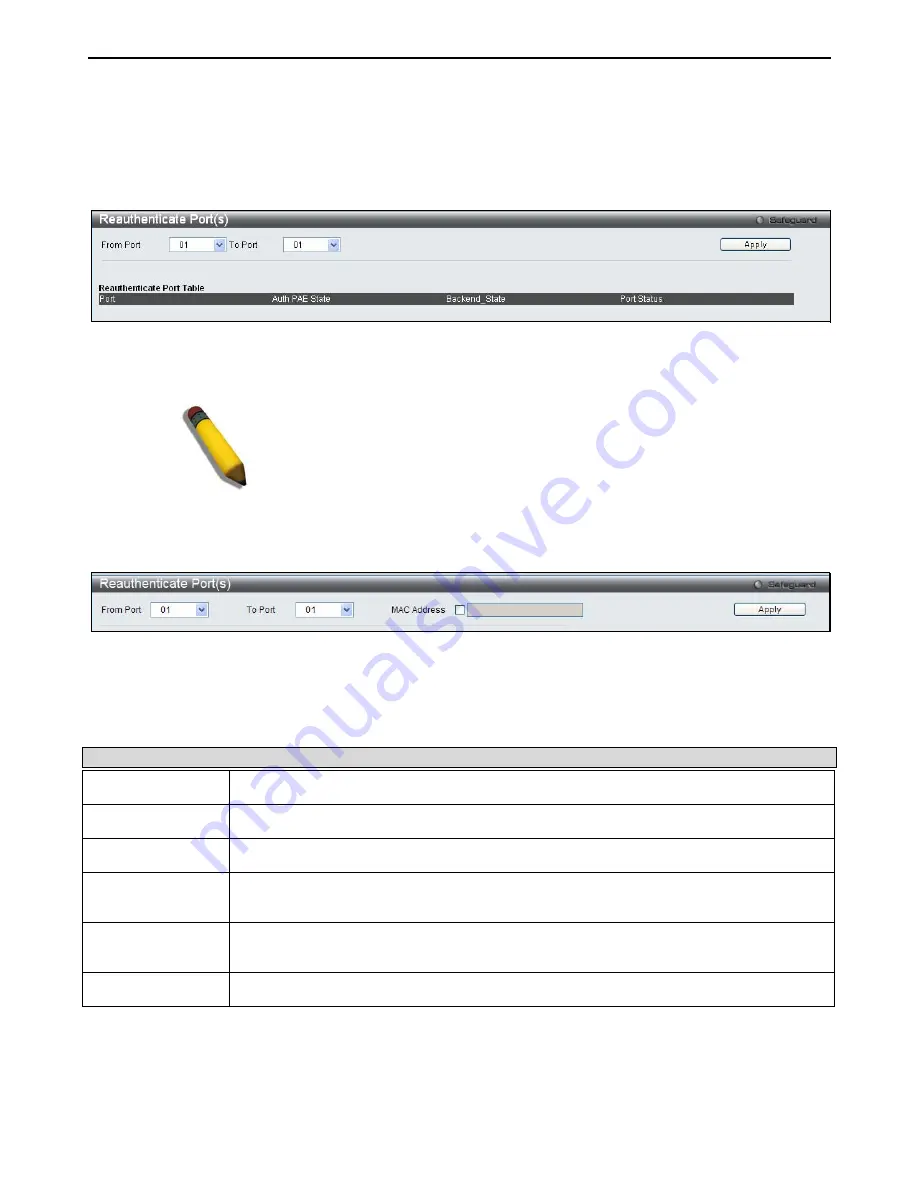
Reauthenticate Port(s)
Users can display and configure reauthenticate ports for 802.1X port and host using the two windows below.
To reauthenticate ports for the port side of 802.1X, the user must first enable 802.1X by port in the
802.1X Settings
window
To view the following window, click
Security > 802.1X > Reauthenticate Port(s)
:
Figure 5 - 27. Reauthenticate Port(s) window for Port-based 802.1X
This window allows reauthentication of a port or group of ports by using the pull-down menus
From Port and To Port and clicking
Apply
. The Reauthenticate Port Table
displays the current status of the reauthenticated port(s) once
Apply
has been clicked
.
NOTE:
The user must first globally enable 802.1X in the
802.1X Settings
window (
Security
>
802.1X
>
802.1X Settings
) before reauthenticating
ports. Information in the
Reauthenticate Port(s)
window cannot be
viewed before enabling 802.1X.
To reauthenticate ports for the host side of 802.1X, the user must first enable 802.1X by MAC address in the
802.1X Settings
window.
To view the following window, click
Security > 802.1X > Reauthenticate Port(s)
:
Figure 5 - 28. Reauthenticate Port(s) window for Host-based 802.1X
To reauthenticate ports, first use the From Port and To Port drop-down menus to choose the range of ports. Then the user must
specify the MAC address to be reauthenticated by entering it into the MAC Address
field and ticking the corresponding check box.
To begin the reauthentication, click
Apply
.
This window displays the following information:
Parameter Description
From Port
The beginning port in a range of ports to be reauthenticated.
To Port
The ending port in a range of ports to be reauthenticated.
MAC Address
Displays the physical address of the Switch where the port resides.
Auth PAE State
The Authenticator State will display one of the following:
Initialize, Disconnected, Connecting,
Authenticating, Authenticated, Aborting, Held, ForceAuth, ForceUnauth,
and
N/A.
Backend_State
The Backend State will display one of the following:
Request, Response, Success, Fail,
Timeout, Idle, Initialize,
and
N/A.
Port Status
The status of the controlled port can be
Authorized, Unauthorized,
or
N/A
.
Содержание DGS-3200-16 - Switch - Stackable
Страница 1: ...Manual ProductModel xStack DGS 3200 Series Layer2ManagedGigabit Ethernet Switch Release 1 35 ...
Страница 235: ......






























