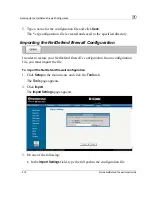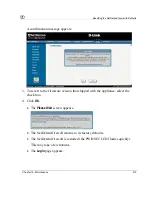
Using Diagnostic Tools
Note:
This element can be pre
page 413 and
udp
on page 414.
P
ARAMETERS
pended by tc
dp. For information, see
tcp
on
r. The port t
packet is sent.
XAMPLE
at are destined for port 80:
p or u
port
Intege
E
o which the
The following filter string saves packets th
dst port 80
to capture packets of a specific ether protocol
YNTAX
er proto
\
protocol
ng. The protocol type of the packet.
wing:
ip, ip6, arp, rarp,
lk, aarp, dec net, sca, lat,
mopdl, moprc, iso, stp, ipx,
or
.
es ARP packets:
ether proto arp
ether proto
P
URPOSE
The
ether proto
element is used
type.
S
eth
P
ARAMETERS
protocol
Stri
This can be the follo
ata
netbeui
E
XAMPLE
The following filter string sav
Chapter 14: Maintenance
409