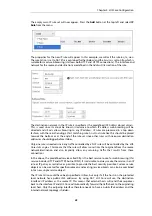
AutoDefaultGatewayRoute:
Yes
ReceiveMulticastTraffic:
Auto
MemberOfRoutingTable:
All
Comments:
<empty>
The typical output from this will be similar to the following:
Setting the default gateway on the interface has the additional effect that cOS Core
automatically creates a route in the default
main
routing table that has the network
all-nets
routed on the interface. This means that we do not need to explicitly create this route.
Even though an
all-nets
route is automatically added, no traffic can flow without the addition of
an
IP rule
which explicitly allows traffic to flow. Let us assume we want to allow web browsing
from the protected network
G1_net
on the interface A simple rule to do this would have the
rule's
Action
property set to the value
Allow
and is defined with the following command:
The IP rule set
main
always exists by default and is a top level CLI context. Add an IP rule called
lan_to_wan
to allow the traffic through to the public Internet:
Device:/> add IPRule Action=Allow
SourceInterface=G1
SourceNetwork=InterfaceAddresses/G1_net
DestinationInterface=G2
DestinationNetwork=all-nets
Service=http
Name=lan_to_wan
This IP rule would be correct if the internal network hosts have public IPv4 addresses but in most
scenarios this will not be true and internal hosts will have private IPv4 addresses. In that case, we
must use NAT to send out traffic so that the apparent source IP address is the IP of the interface
connected to the ISP. To do this we simply change the
Action
property in the above command
from a value of
Allow
to a value of
NAT
:
Device:/main> add IPRule Action=NAT
SourceInterface=G1
SourceNetwork=InterfaceAddresses/G1_net
DestinationInterface=G2
DestinationNetwork=all-nets
Service=http
Name=lan_to_wan
The service used in the IP rule is
http
which will allow most web browsing but does not include
the DNS protocol to resolve URLs into IP addresses. To solve this problem, a custom service could
be used in the above rule which combines
http
with the
dns-all
service. However, the
recommended method which provides the most clarity to a configuration is to create a separate
IP rule for DNS:
Device:/main> add IPRule Action=NAT
SourceInterface=G1
SourceNetwork=InterfaceAddresses/G1_net
DestinationInterface=G2
DestinationNetwork=all-nets
Service=dns-all
Name=lan_to_wan_dns
It is recommended that at least one DNS server is also defined in cOS Core. This DSN server or
servers (a maximum of three can be configured) will be used when cOS Core itself needs to
resolve URLs which will be the case when a URL is specified in a configuration instead of an IP
address. If we assume an IP address object called
dns1_address
has already been defined for the
first DNS server, the command to specify the first DNS server is:
Device:/> set DNS DNSServer1=dns1_address
Chapter 4: cOS Core Configuration
56
Содержание Eagle E20
Страница 10: ...Chapter 1 E20 Product Overview 10 ...
Страница 25: ...Chapter 3 E20 Installation 25 ...
Страница 67: ...Chapter 4 cOS Core Configuration 67 ...
Страница 76: ...Clavister AB Sjögatan 6J SE 89160 Örnsköldsvik SWEDEN Phone 46 660 299200 www clavister com ...