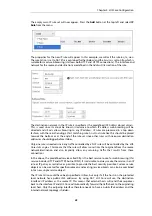
The IP rule again has the
NAT
action and this is necessary if the protected local hosts have private
IPv4 addresses. The ICMP requests will be sent out from the Clavister Security Gateway with the
IP address of the interface connected to the ISP as the source interface. Responding hosts will
send back ICMP responses to this single IP and cOS Core will then forward the response to the
correct private IPv4 address.
Adding a Drop All Rule
The top-down nature of the IP rule set scanning has already been discussed earlier. If no
matching IP rule is found for a new connection then the
default rule
is triggered. This rule is
hidden and cannot be changed and its action is to drop all such traffic as well as generate a log
message for the drop.
In order to gain control over the logging of dropped traffic, it is recommended to create a drop
all rule as the last rule in the
main
IP rule set. This rule has an
Action
of
Drop
with the source and
destination network set to
all-nets
and the source and destination interface set to
any
.
The service for this rule must also be specified and this should be set to
all_services
in order to
capture all types of traffic.
If the this rule us the only one defined, displaying the
main
IP rule set will be as shown below.
Chapter 4: cOS Core Configuration
50
Содержание Eagle E20
Страница 10: ...Chapter 1 E20 Product Overview 10 ...
Страница 25: ...Chapter 3 E20 Installation 25 ...
Страница 67: ...Chapter 4 cOS Core Configuration 67 ...
Страница 76: ...Clavister AB Sjögatan 6J SE 89160 Örnsköldsvik SWEDEN Phone 46 660 299200 www clavister com ...