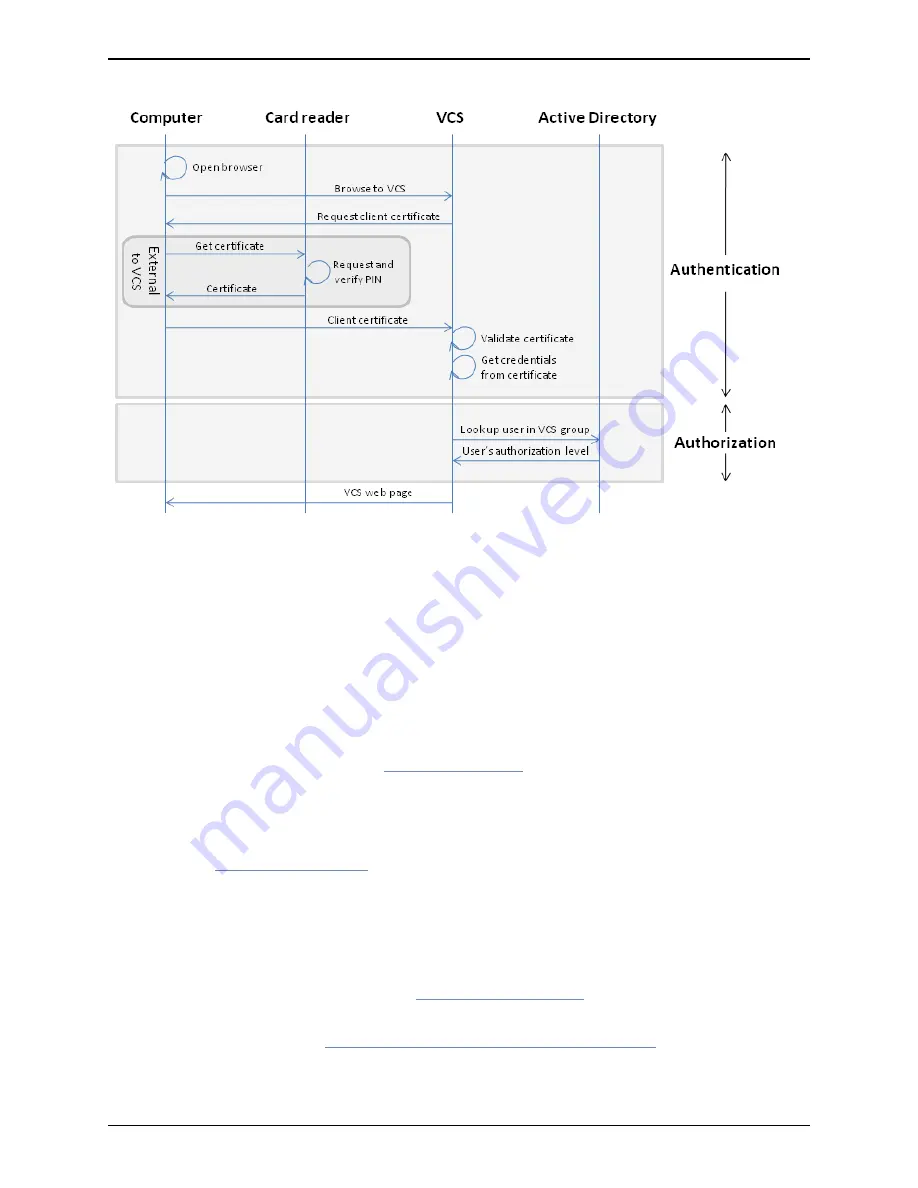
Note that if the client certificate is not protected (by a PIN or some other mechanism) then unauthenticated
access to the VCS may be possible. This lack of protection may also apply if the certificates are stored in the
browser, although some browsers do allow you to password protect their certificate store.
Obtaining the username from the certificate
The username is extracted from the client browser's certificate according to the patterns defined in the
Regex
and
Username format
fields on the
Certificate-based authentication configuration
page:
n
In the
Regex
field, use the
(?<name>regex)
syntax to supply names for capture groups so that
matching sub-patterns can be substituted in the associated
Username format
field, for example,
/(Subject:.*, CN=(?<Group1>.*))/m
.
The regex defined here must conform to
PHP regex guidelines
.
n
The
Username format
field can contain a mixture of fixed text and the capture group names used in the
Regex
. Delimit each capture group name with
#
, for example,
prefix#Group1#suffix
. Each capture
group name will be replaced with the text obtained from the regular expression processing.
You can use the
Client certificate testing
page to test the outcome of applying different
Regex
and
Username format
combinations to a certificate.
Testing client certificates
The
Client certificate testing
page (
Maintenance > Security certificates > Client certificate testing
) is
used to check client certificates before enabling
client certificate validation
. You can:
n
Test whether a client certificate is valid when checked against the VCS's current trusted CA list and, if
loaded, the revocation list (see
Managing certificate revocation lists (CRLs) [p.288]
).
Cisco VCS Administrator Guide (X8.1.1)
Page 292 of 507
Maintenance
About security certificates
















































