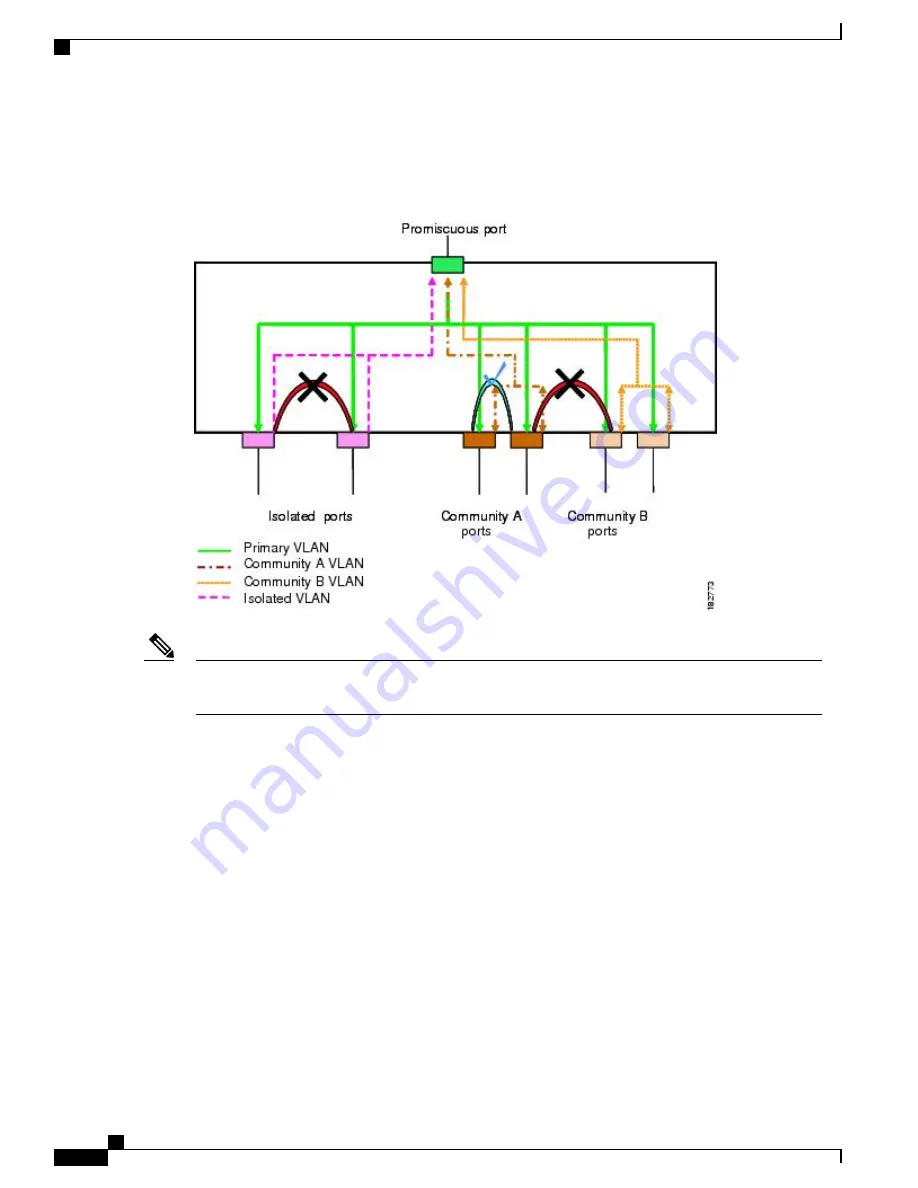
The following figure shows the traffic flow within a PVLAN, along with the types of VLANs and types of
ports.
Figure 5: Private VLAN Traffic Flows
The PVLAN traffic flows are unidirectional from the host ports to the promiscuous ports. Traffic received
on primary VLAN enforces no separation and forwarding is done as in a normal VLAN.
Note
A promiscuous access port can serve only one primary VLAN and multiple secondary VLANs (community
and isolated VLANs). A promiscuous trunk port can carry traffic for several primary VLANs. Multiple
secondary VLANs under a given primary VLAN can be mapped to promiscuous trunk ports. With a
promiscuous port, you can connect a wide range of devices as access points to a PVLAN. For example, you
can use a promiscuous port to monitor or back up all the PVLAN servers from an administration workstation.
In a switched environment, you can assign an individual PVLAN and associated IP subnet to each individual
or common group of end stations. The end stations need to communicate only with a default gateway to
communicate outside the private VLAN.
Associating Primary and Secondary VLANs
To allow host ports in secondary VLANs to communicate outside the PVLAN, you associate secondary
VLANs to the primary VLAN. If the association is not operational, the host ports (community and isolated
ports) in the secondary VLAN are brought down.
Cisco Nexus 6000 Series NX-OS Layer 2 Switching Configuration Guide, Release 7.x
32
Configuring Private VLANs
Primary, Isolated, and Community Private VLANs
















































